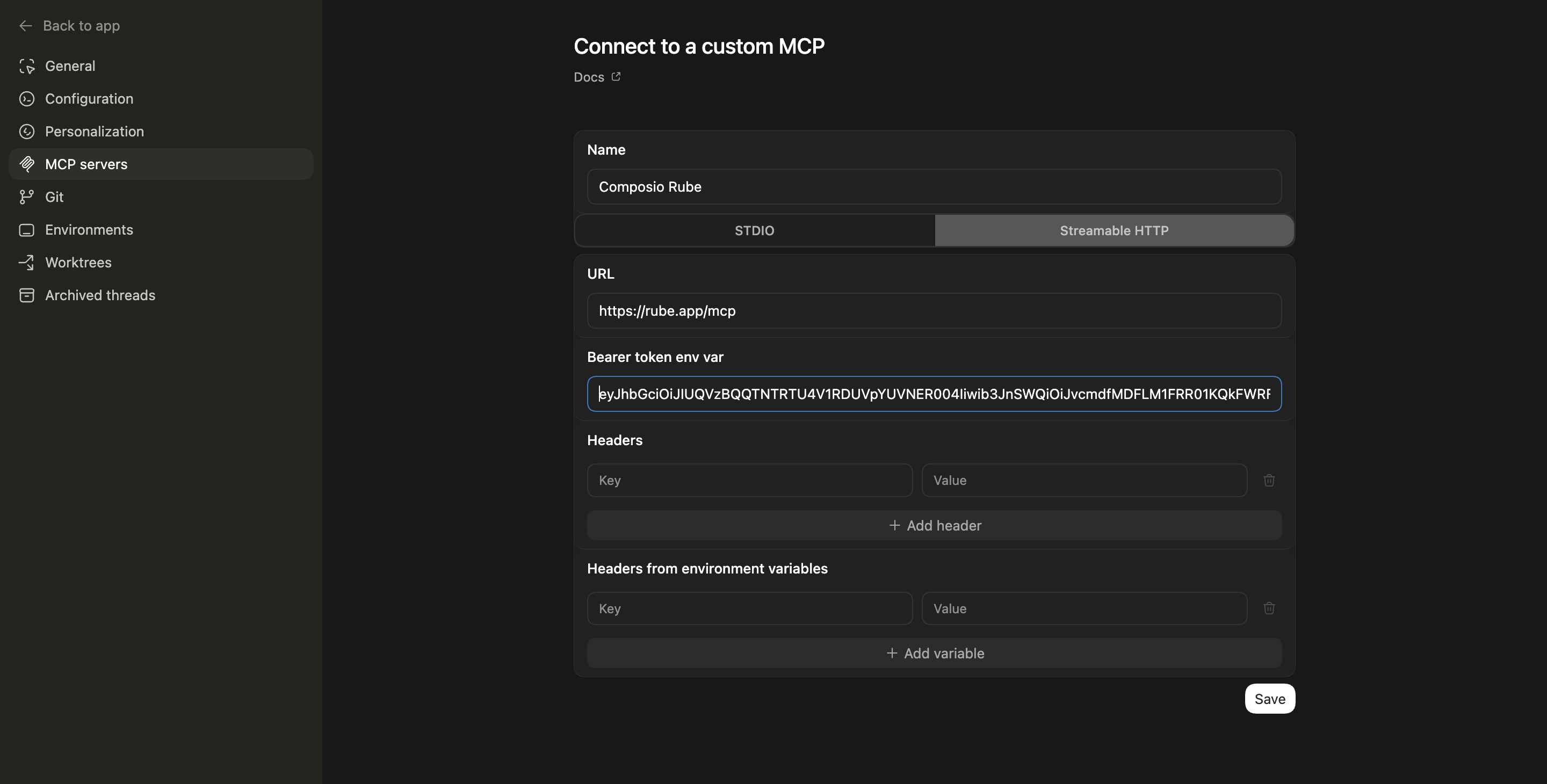
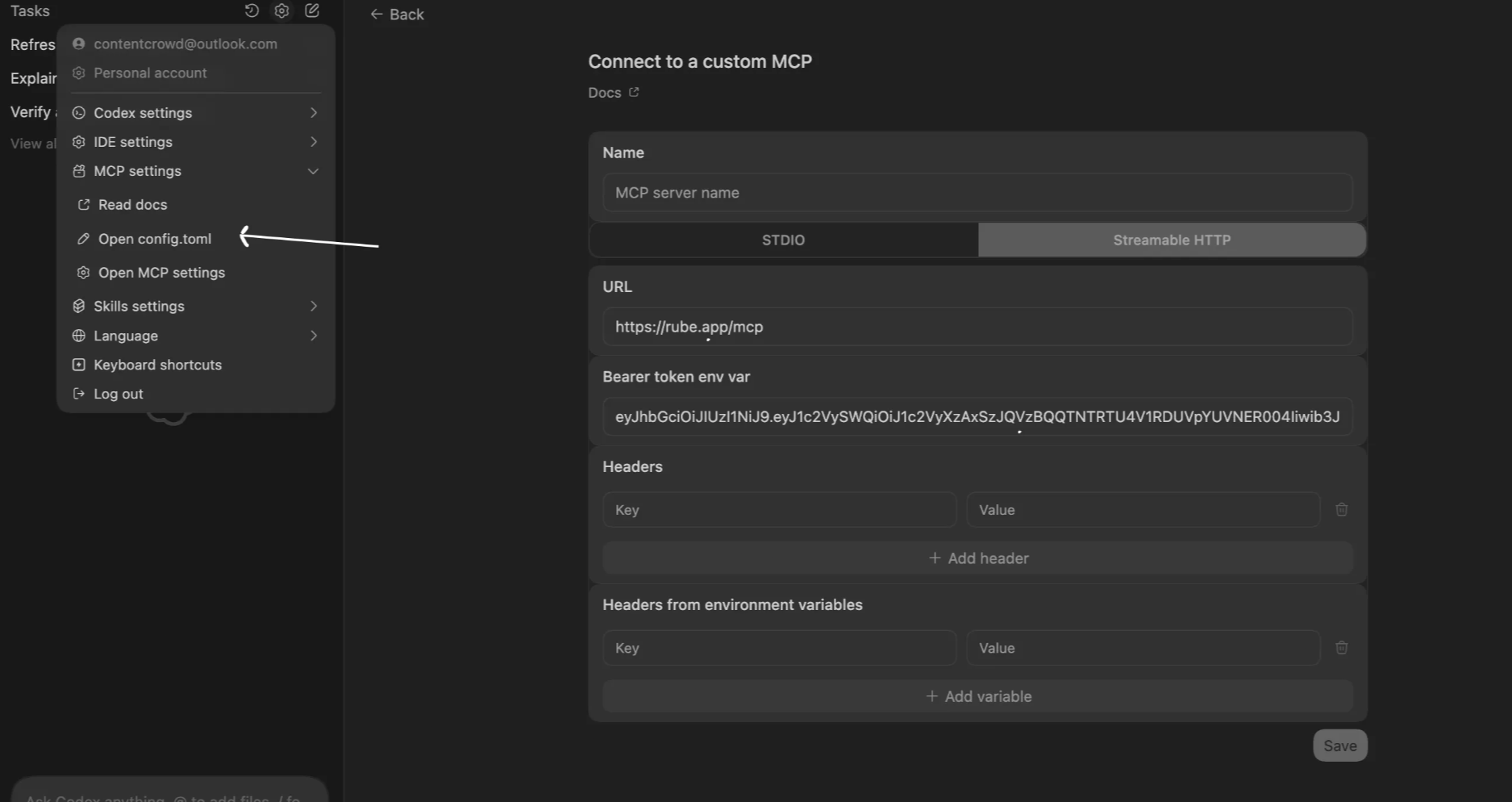
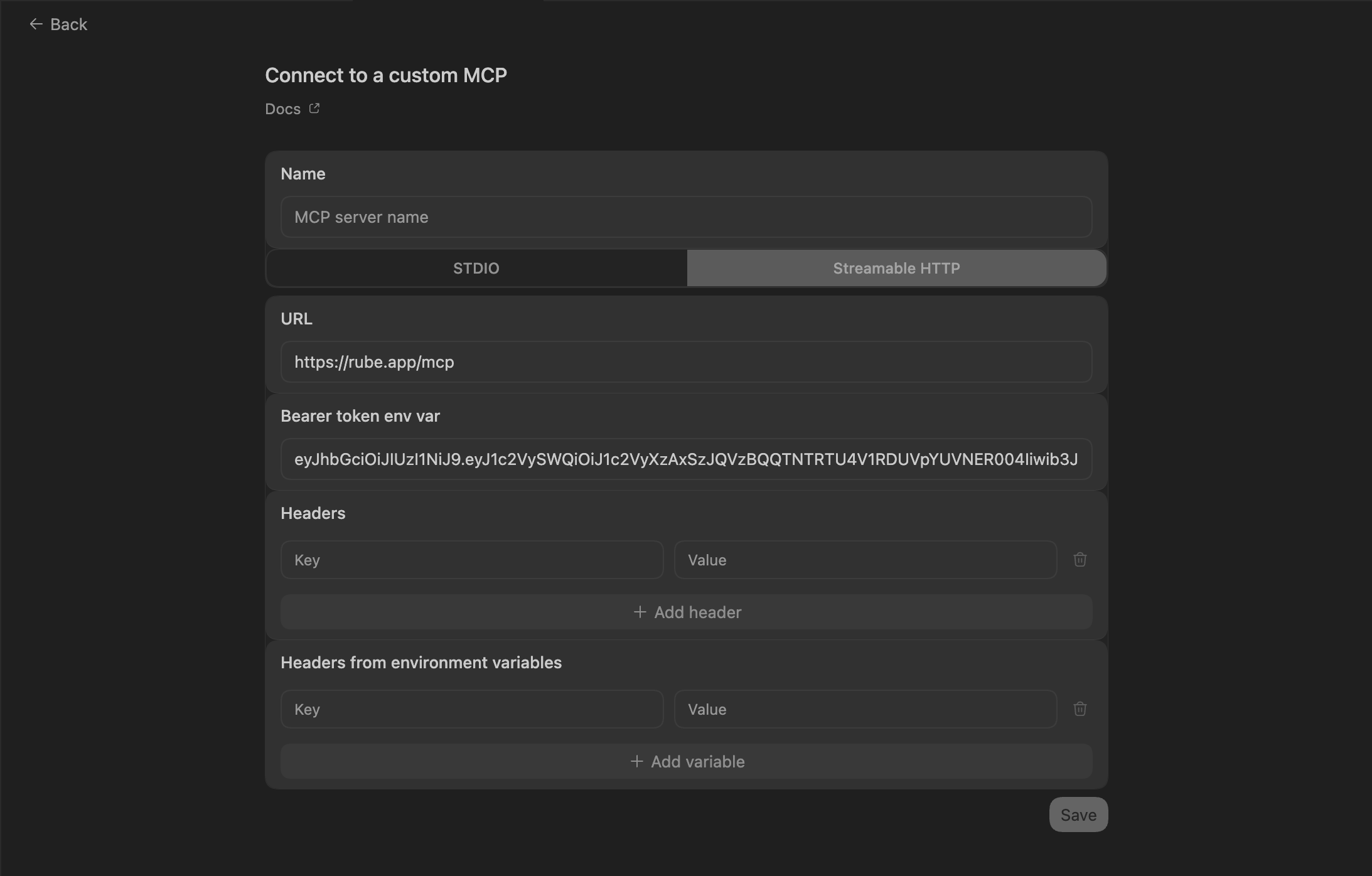
Create ApplicationTool to create a new svix application.
Delete Svix ApplicationTool to delete an application by its id.
Get ApplicationTool to retrieve details of a specific svix application by its id.
List ApplicationsTool to list all applications.
Update Svix ApplicationTool to update an existing svix application by id.
Get Attempt DetailsTool to retrieve details of a specific message attempt.
List Message AttemptsTool to list all delivery attempts for a specific message.
Create EndpointTool to create a new svix webhook endpoint.
Delete EndpointTool to delete an endpoint.
Get EndpointTool to retrieve details of a specific endpoint.
List EndpointsTool to list all endpoints for a specific application.
Patch EndpointTool to partially update an endpoint’s configuration.
Patch Endpoint HeadersTool to partially update headers for a specific endpoint.
Recover Failed WebhooksTool to recover messages that failed to send to an endpoint.
Replay Missing WebhooksTool to replay missing webhooks for a specific endpoint.
Get Endpoint SecretTool to retrieve the secret for a specific endpoint.
Rotate Endpoint SecretTool to rotate the signing secret key for an endpoint.
Send Example MessageTool to send a test message for a specific event type to an endpoint.
Get Endpoint StatsTool to retrieve basic statistics for a specific endpoint.
Get Endpoint TransformationTool to retrieve transformation settings for a specific endpoint.
Set Endpoint TransformationTool to set or update transformation settings for an endpoint.
Update EndpointTool to update an existing endpoint.
Update Endpoint HeadersTool to completely replace headers for a specific endpoint.
Create Event TypeTool to create a new event type or unarchive an existing one.
Delete Event TypeTool to delete an event type.
Get Event TypeTool to retrieve details of a specific event type by its id.
List Event TypesTool to retrieve a list of all event types.
Update Event TypeTool to update an existing event type by id.
Create IntegrationTool to create a new integration for a specific application.
Delete IntegrationTool to delete an integration.
Get IntegrationTool to retrieve details of a specific integration.
List IntegrationsTool to list all integrations for a specific application.
Update IntegrationTool to update an existing integration by id.
Create MessageTool to create a new message for a specific application in svix.
Get MessageTool to retrieve details of a specific message by its id.
List MessagesTool to list all messages for a specific application.
Create SourceTool to create a source for message ingestion.