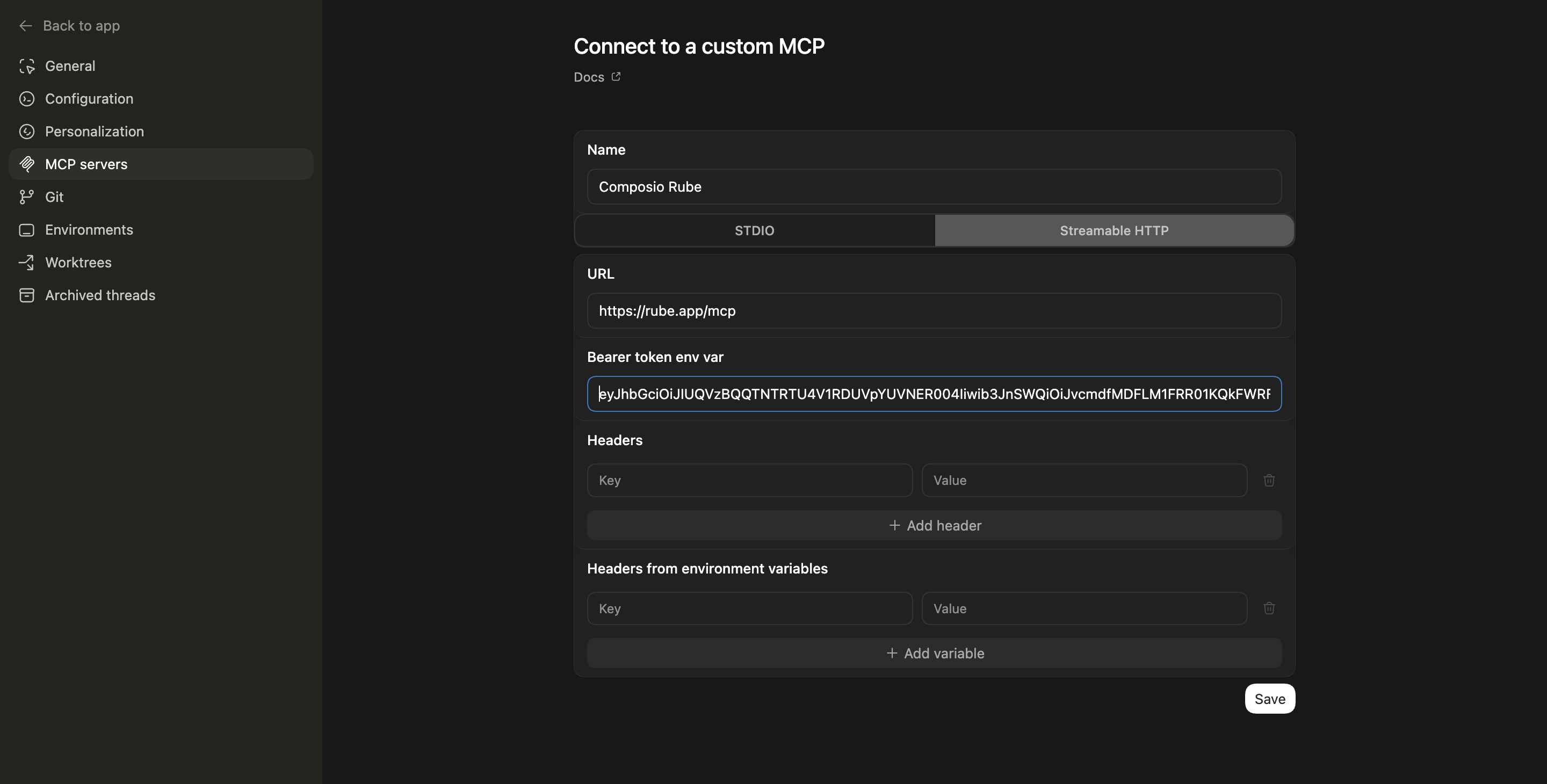
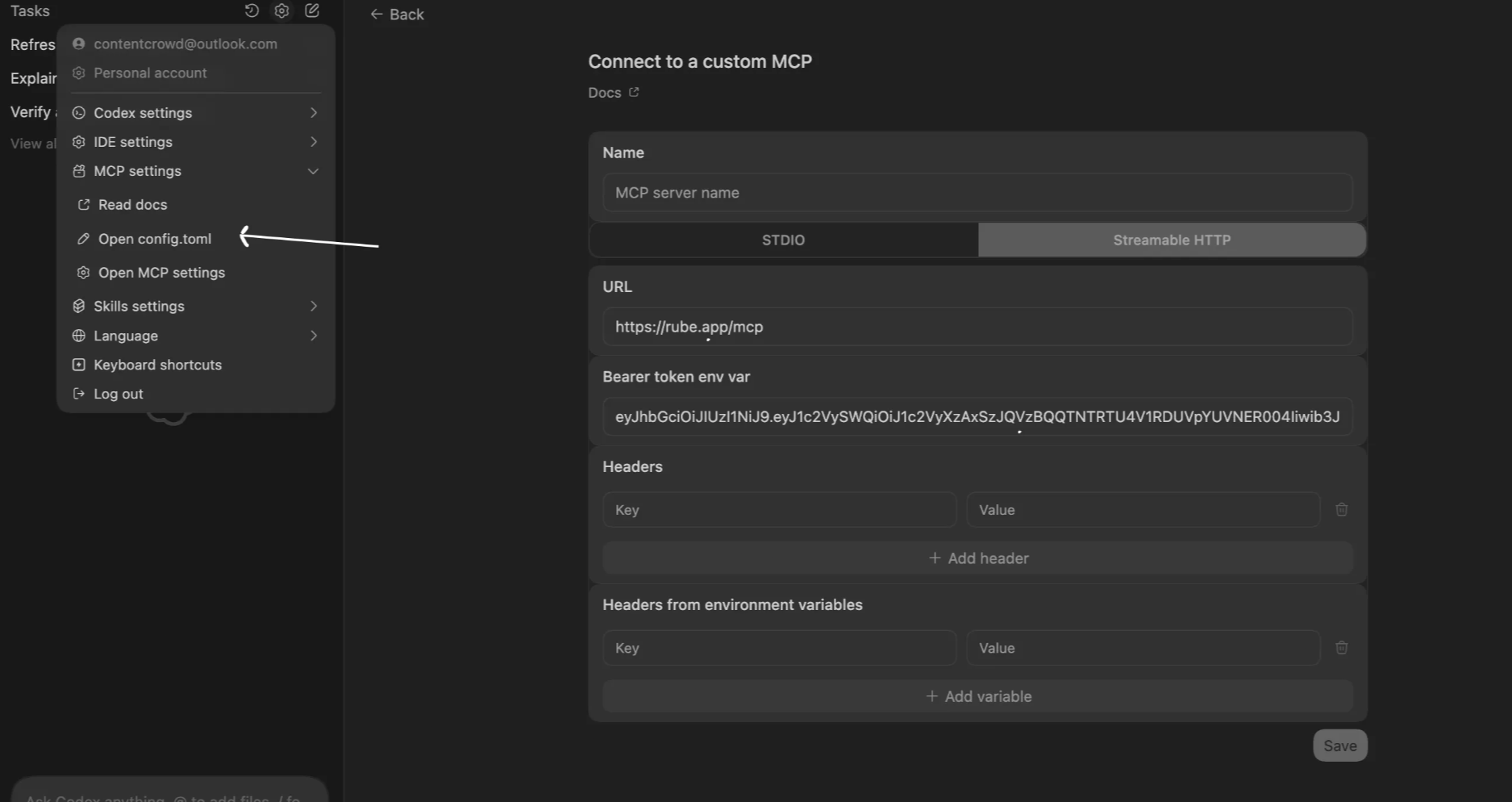
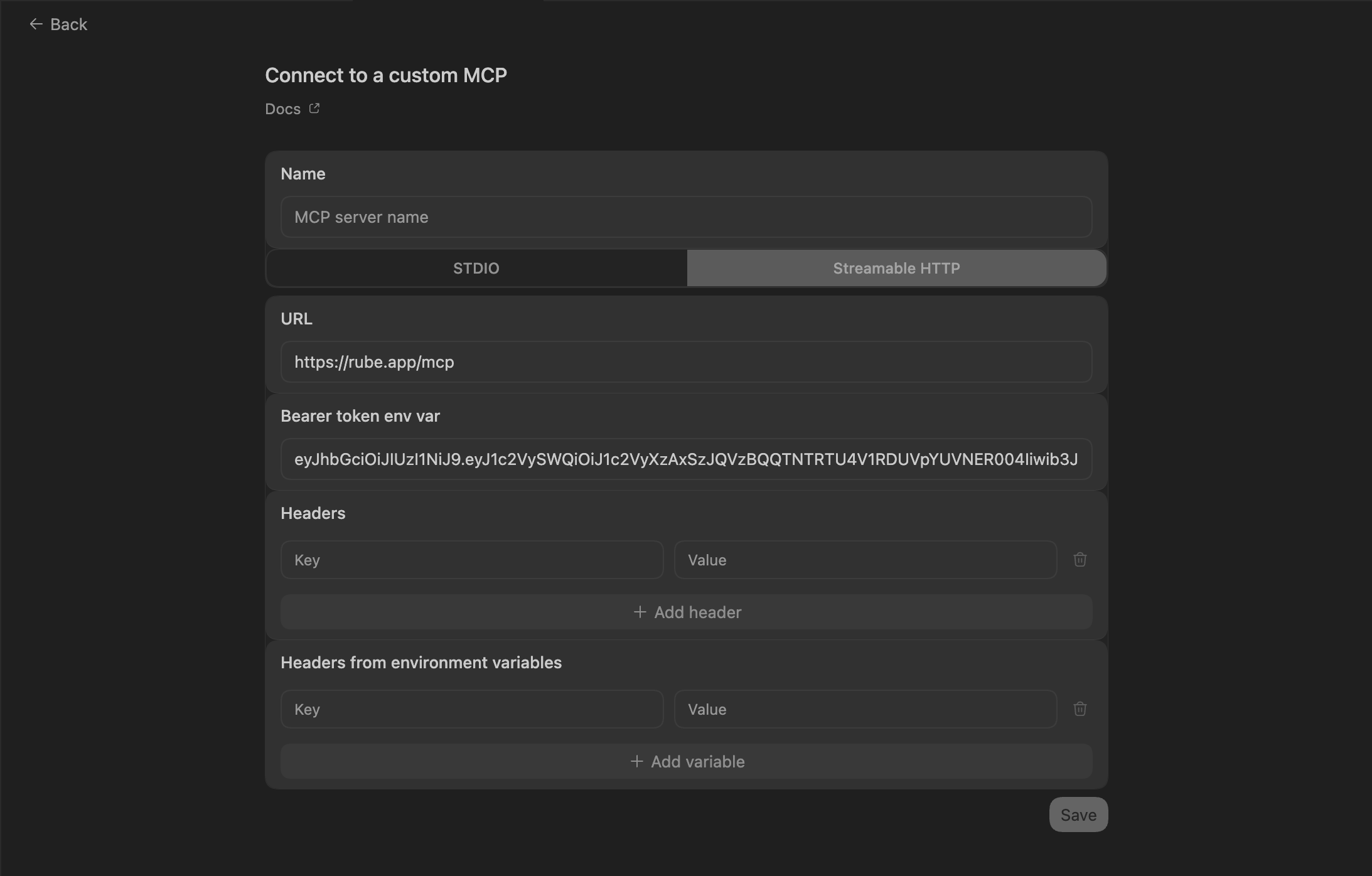
Create DNS RecordTool to create a new DNS record in a Cloudflare zone.
Create Zone Lockdown RuleTool to create a Zone Lockdown rule.
Create Rule in RulesetTool to add a rule to an existing ruleset.
Create RulesetTool to create an account- or zone-scoped ruleset.
Delete DNS RecordTool to delete a DNS record.
Delete DNSSECTool to delete DNSSEC records for a zone.
Delete Rule from RulesetTool to delete a specific rule from a ruleset.
Delete RulesetTool to delete all versions of a ruleset.
Delete a zoneTool to delete an existing zone.
Get Entrypoint Ruleset VersionTool to get a specific version of an entry point ruleset.
Get Lockdown RuleTool to get a Zone Lockdown rule.
Get Regional Tiered CacheTool to get the regional tiered cache setting for a zone.
Get RulesetTool to fetch the latest version of a ruleset by ID.
Get Zone DetailsTool to get details for a specific zone.
List DNS RecordsTool to list DNS records for a given Cloudflare zone.
List Cloudflare ZonesTool to list, search, sort, and filter Cloudflare zones.
Overwrite DNS RecordTool to completely overwrite a DNS record.
Rerun Zone Activation CheckTool to trigger a new activation check for a PENDING zone.
Update DNSSEC StatusTool to update DNSSEC configuration for a zone.
Update Lockdown RuleTool to update a zone lockdown rule.
Update Rule in RulesetTool to update a specific rule in a ruleset.
Update RulesetTool to update a Cloudflare ruleset, creating a new version.
Update Cloudflare ZoneTool to edit a Cloudflare zone.
Upload File to S3Tool to upload arbitrary file content to the app’s temporary R2/S3 bucket.