
Top 5 secure OpenClaw Alternatives to consider
Top 5 secure OpenClaw Alternatives to consider
OpenClaw is everywhere right now, and I get the hype. I’ve been seeing it all over my feed lately, and it’s clearly clicking with a lot of people.
After using it for quite some time myself, it feels a bit too noisy, and not every tool works the same way for every person.
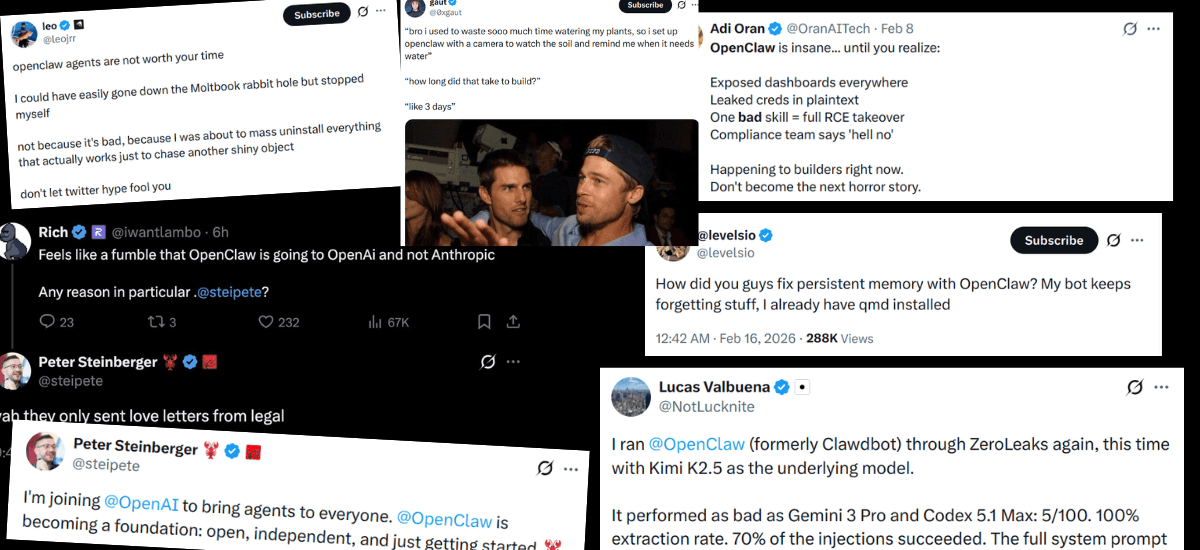
Whenever something starts trending this hard, it’s a good excuse to look around, especially if you’re after something more minimal.
And now, OpenClaw may have its 4th rename to be ClosedClaw very soon. You never know with OpenAI.
TL;DR
If OpenClaw feels like too much, these are the cleaner picks: TrustClaw if you want secure cloud actions, ZeroClaw if you want Rust speed, NanoClaw if you want container isolation, nanobot if you want a tiny readable codebase, and memU Bot if you want proactive memory that improves over time.
One line summary for each tool:
TrustClaw: Cloud agent rebuilt around OAuth + sandboxed execution with 1000+ tools, so you get actions without running risky stuff locally.
ZeroClaw: Rust framework built for speed with a <10ms startup, 3.4MB binary, and 22+ providers.
NanoClaw: Runs agents in real OS-level containers (Apple Container or Docker) so each chat stays isolated instead of sharing one process.
nanobot: A full agent in about ~4,000 LOC with a live line counter, plus MCP support, so tools plug in cleanly.
memU Bot: A proactive assistant built on memU’s memory engine, designed for long-running agents and lower context cost, with a simple email-download install flow.
Why OpenClaw alternatives?
OpenClaw is super powerful, no doubt, but it comes with two big headaches that you've probably already felt.
Security
Setup Friction
Security
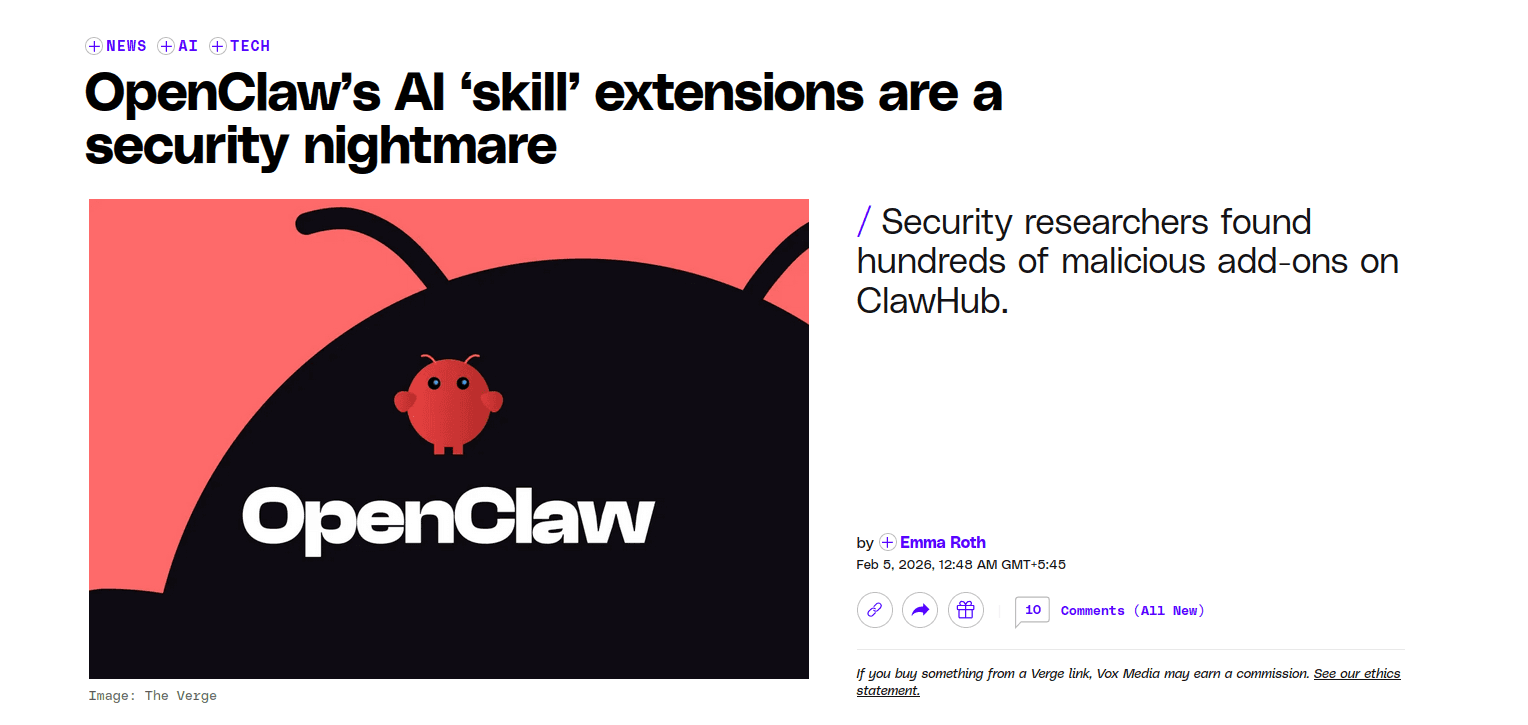
When your agent can read files, run shell commands, and pull in third-party “skills,” you are basically giving it the keys to your machine. The skill marketplace has already turned into a real problem, with researchers finding hundreds of malicious skills.
If you are not auditing everything you install, it is easy to get yourself cooked. A full security coverage on it: OpenClaw: Security Nightmare Dressed Up as a Day Dream
Setup Friction
The “self-host it and wire up” path is fun if you like tinkering, but it is also where most people get stuck. You end up handling gateways, background services, tokens, and permission issues (most of the time).
And it's not that you're probably going to use all the features that come with the bloated app, just a few, for most people, so alternatives often could be a good choice.
Below are five OpenClaw alternatives that can cover the same ground, often with a smoother and more minimal experience, depending on what you’re building.
Best OpenClaw Alternatives to Consider
1. TrustClaw
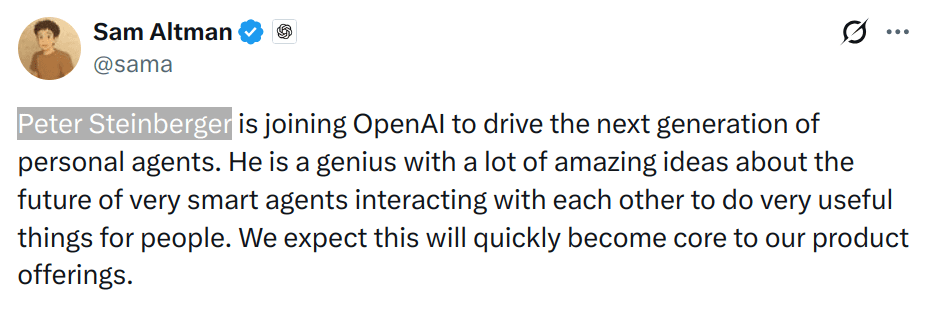
ℹ️ Rebuilt from scratch on OpenClaw's idea with 20000+ tools, with a focus on security and ease of use.
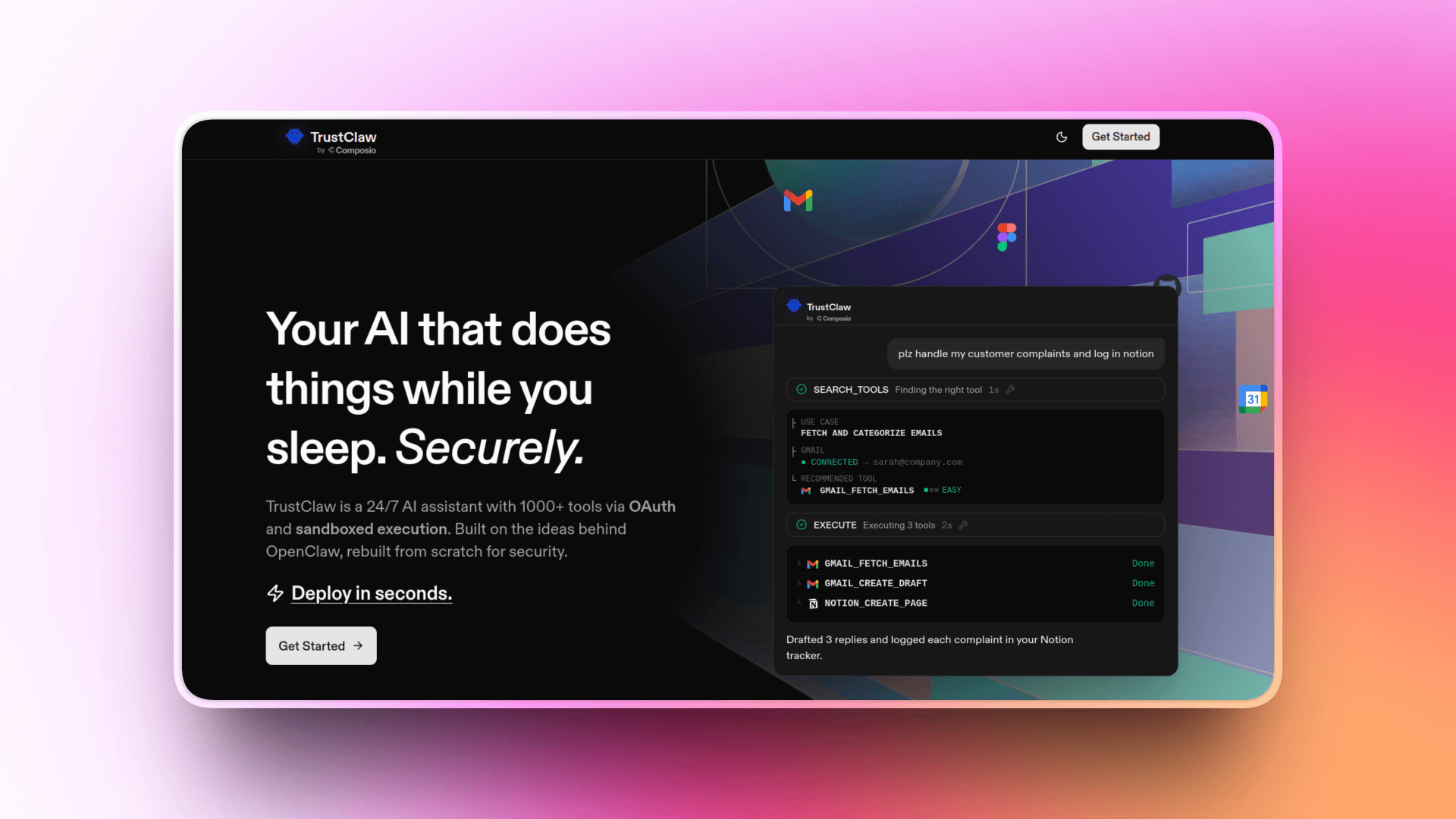
TrustClaw is for those who like the idea of OpenClaw but don't want to hand over their passwords to the agent and run it locally.
It's built by the Composio team, and the pitch is basically: you get an agent that is available 24/7, capable of taking real actions across a vast number (500+) of apps, but the risky parts like credentials and code execution are handled in a more controlled way.
What makes it different?
OAuth-only auth: You connect apps the normal way (OAuth), so you don't paste API keys or passwords into config files.
Sandboxed execution by default: Every action runs in an isolated cloud environment that disappears when the task finishes. So you are not running “agent code” locally with your permissions.
Managed tool surface: Instead of pulling random community “skills” from a public registry, TrustClaw uses Composio’s managed integrations and tooling.
Audit trails + kill switch: It keeps a full audit log, and you can revoke access with one click if needed.
The last point is important because agent toolchains are a real security risk right now. These marketplaces, with just one random add-on, can trick you into running malware. This has already happened. Ref: OpenClaw’s AI ‘skill’ extensions are a security nightmare
The kind of prompts it’s built for
“Handle my customer complaints and log in Notion”
It finds the right tools, fetches emails, creates drafts, and writes Notion pages (using tools such as:
GMAIL_FETCH_EMAILS,GMAIL_CREATE_DRAFT,NOTION_CREATE_PAGE).“Pull all Reddit threads mentioning [competitor] from the last 3 months, analyze sentiment...”
“Summarize all Slack messages in #product-feedback from this week...”
Why it’s comparatively better (for most of you)
Set up in seconds (vs. 30 to 60 minutes of tunnels and local setup)
Encrypted credentials managed by Composio (vs. plaintext local config)
Remote sandbox (vs. local machine execution)
Managed tool surface (vs. unvetted public skill registry)
Action logs + one-click revocation (vs. digging through config files)
and no need for Mac Mini 🤷♂️
Quick start
Go to TrustClaw and hit Get Started.
Connect the apps you want (OAuth flow).
Give it a task in plain language, or schedule one to run while you are offline.
Here's a demo: 👇

It's that simple: now you have OpenClaw running completely in the cloud, with managed permissions and the tools you require.
2. ZeroClaw
ℹ️ Written in Rust, it runs even on $10 hardware with <5MB RAM.
ZeroClaw keeps the agent stack lean. Instead of a big local setup with lots of moving parts, you get a lightweight Rust binary that starts fast and runs comfortably on cheap hardware. If you care more about speed, stability, and low resource use, this one hits the sweet spot.
What makes it different?
Ultra lightweight: designed to keep CPU and RAM usage low.
Quick boot: fast startup, good for bots and always-on tasks.
Modular: swap models, memory, tools, and channels without rewriting everything.
Why pick it over OpenClaw?
You want something minimal and predictable.
You’re running on a small VPS / Raspberry Pi / home lab.
You don’t need a huge plugin marketplace; you need a tool that just runs.
Quick Start
git clone https://github.com/zeroclaw-labs/zeroclaw.git cd zeroclaw cargo build --release cargo install --path . --force # quick setup with openrouter zeroclaw onboard --api-key sk-... --provider openrouter # chat zeroclaw agent -m "Hello, ZeroClaw!"
git clone https://github.com/zeroclaw-labs/zeroclaw.git cd zeroclaw cargo build --release cargo install --path . --force # quick setup with openrouter zeroclaw onboard --api-key sk-... --provider openrouter # chat zeroclaw agent -m "Hello, ZeroClaw!"
git clone https://github.com/zeroclaw-labs/zeroclaw.git cd zeroclaw cargo build --release cargo install --path . --force # quick setup with openrouter zeroclaw onboard --api-key sk-... --provider openrouter # chat zeroclaw agent -m "Hello, ZeroClaw!"
Here's a quick architecture overview for those who care: 👇

3. NanoClaw
ℹ️ OpenClaw's alternative that runs entirely in a container for security.

NanoClaw is basically the same thing but runs completely isolated inside a Docker container. The whole idea is simple: keep the codebase small, and put the risky stuff (bash, file access, tools) inside an isolated container so it can only touch what you explicitly mount.
That's pretty much the idea of NanoClaw.
What makes it different?
Container isolation by default: runs in Apple Container (macOS) or Docker (macOS/Linux), with filesystem isolation.
Per-chat sandboxing: each group/chat can have its own memory and its own mounted filesystem, separated from others.
Built on Anthropic’s Agents SDK: it’s basically designed to work nicely with Claude’s agent tooling and Claude Code.
WhatsApp + scheduled jobs: message it from your phone, and set recurring tasks that ping you back.
Quick start
git clone https://github.com/gavrielc/nanoclaw.git cd
git clone https://github.com/gavrielc/nanoclaw.git cd
git clone https://github.com/gavrielc/nanoclaw.git cd
Then run /setup. Claude Code handles everything: dependencies, authentication, container setup, and service configuration.
Here's a quick demo: 👇

4. nanobot
ℹ️ Ultra lightweight AI assistant built with Python.

Nanobot, as the name suggests, is quite small. The core agent is about ~4,000 lines of code, and the repo even publishes a live count you can verify with their script. That is the whole vibe: small enough that you can actually read it, trust it, and change it.
What makes it different?
Core size metric: ~4,000 LOC, with a “real-time” line count shown in the README (and a script to verify).
MCP support (fresh): added 2026-02-14, so it can plug into MCP tool servers without you reinventing the plumbing.
Runs where you already are: built-in “gateway” mode supports a bunch of chat surfaces like Telegram, Discord, WhatsApp, Slack, Email, and more.
Quick Start
pip install nanobot-ai nanobot onboard nanobot agent # local interactive chat nanobot gateway # run it as a chat bot (Telegram, Discord, WhatsApp, etc)
pip install nanobot-ai nanobot onboard nanobot agent # local interactive chat nanobot gateway # run it as a chat bot (Telegram, Discord, WhatsApp, etc)
pip install nanobot-ai nanobot onboard nanobot agent # local interactive chat nanobot gateway # run it as a chat bot (Telegram, Discord, WhatsApp, etc)
Here's a quick architecture:
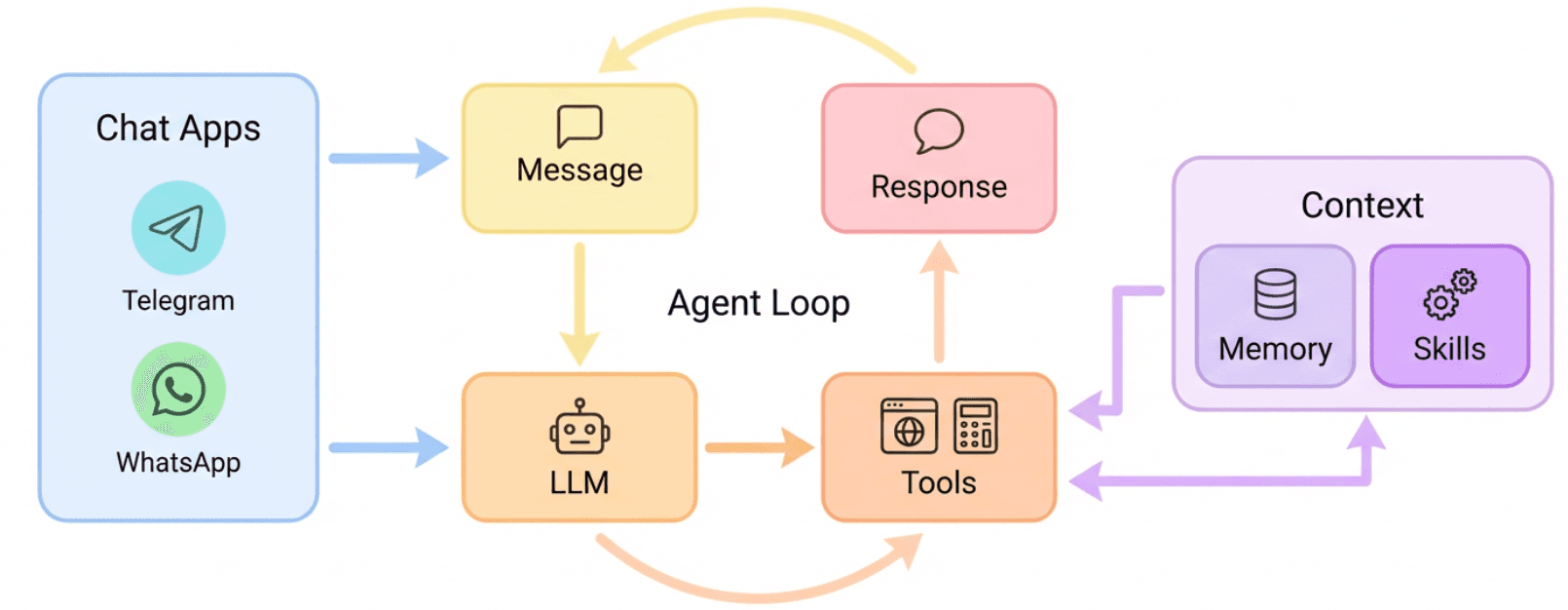
Here's a video to give you an idea of how it works: 👇

5. memU Bot
ℹ️ Built for 24/7 proactive agents designed for long-running use.
memU Bot is built for people who want an agent that keeps running and becomes more useful over time, instead of resetting to zero every time you open a new chat.
The site definitely looks like it was coded by a 12-year-old, but don’t let that scare you off, because the product underneath is really good.
Under the hood, it’s tied to memU, NevaMind’s memory framework for long-running proactive agents, with a focus on reducing long-run context cost by caching insights.
What makes it different?
Always-on + proactive: it’s designed to sit in the background and capture intent (not just respond to prompts).
Memory system that scales: memU treats memory like a file system (categories, memory items, cross-links), so the agent can fetch relevant fragments instead of shoving the whole history into every request.
Quick start
It's a bit more involved than other options.
If you just want the product (memU Bot):
Go to memu.bot, enter your email, and get the download link they send you.
Install it like a normal desktop app (they provide a macOS .dmg in the tutorial flow).
Start it, connect the channel you want (Telegram, etc.), and let it run so it can build memory over time.
git clone <https://github.com/NevaMind-AI/memU.git> cd memU # Requires Python 3.13+ pip install -e . # set your key (OpenAI is the default in their quick tests) export OPENAI_API_KEY="your_api_key" # quick test using in-memory storage cd
git clone <https://github.com/NevaMind-AI/memU.git> cd memU # Requires Python 3.13+ pip install -e . # set your key (OpenAI is the default in their quick tests) export OPENAI_API_KEY="your_api_key" # quick test using in-memory storage cd
git clone <https://github.com/NevaMind-AI/memU.git> cd memU # Requires Python 3.13+ pip install -e . # set your key (OpenAI is the default in their quick tests) export OPENAI_API_KEY="your_api_key" # quick test using in-memory storage cd
Want persistent memory backed by Postgres + pgvector?
docker run -d \ --name memu-postgres \ -e POSTGRES_USER=postgres \ -e POSTGRES_PASSWORD=postgres \ -e POSTGRES_DB=memu \ -p 5432:5432 \ pgvector/pgvector:pg16 export OPENAI_API_KEY="your_api_key" cd
docker run -d \ --name memu-postgres \ -e POSTGRES_USER=postgres \ -e POSTGRES_PASSWORD=postgres \ -e POSTGRES_DB=memu \ -p 5432:5432 \ pgvector/pgvector:pg16 export OPENAI_API_KEY="your_api_key" cd
docker run -d \ --name memu-postgres \ -e POSTGRES_USER=postgres \ -e POSTGRES_PASSWORD=postgres \ -e POSTGRES_DB=memu \ -p 5432:5432 \ pgvector/pgvector:pg16 export OPENAI_API_KEY="your_api_key" cd
They also provide a small runnable "proactive loop" example if you want to see the behaviour without going through tests:
cd
cd
cd
There's also a Cloud version you can try.

That concludes this article. Thank you so much for reading! 🫡
Frequently Asked Questions
What’s the simplest OpenClaw alternative if I just want things to work fast?
If you want the least setup pain, TrustClaw is the most “plug in and go” because it’s cloud-hosted, uses OAuth, and handles execution plus permissions for you. If you want something lightweight you can run yourself, ZeroClaw is the fastest path to a minimal local agent.
Which option is best if I’m mainly worried about security?
Two strong directions: TrustClaw if you want cloud sandboxing, OAuth-only auth, audit logs, and quick revocation, or NanoClaw if you prefer hard isolation via real containers where the agent only touches what you mount. If you’re worried about sketchy skill marketplaces, both avoid the “install random skills” trap in different ways.
I want something minimal and hackable. What should I pick?
Go with nanobot if you want a small, readable codebase you can actually modify without getting lost, plus MCP support for plugging in tools cleanly. ZeroClaw is also minimal, but it’s optimized more for performance and stability than “read the whole repo in a weekend.”
Which one makes the most sense for long-running agents that improve over time?
That’s memU Bot. It’s built around proactive memory so it can get more useful as it runs, while keeping context costs down by retrieving only relevant memory instead of replaying entire chat history.
OpenClaw is everywhere right now, and I get the hype. I’ve been seeing it all over my feed lately, and it’s clearly clicking with a lot of people.
After using it for quite some time myself, it feels a bit too noisy, and not every tool works the same way for every person.

Whenever something starts trending this hard, it’s a good excuse to look around, especially if you’re after something more minimal.
And now, OpenClaw may have its 4th rename to be ClosedClaw very soon. You never know with OpenAI.

TL;DR
If OpenClaw feels like too much, these are the cleaner picks: TrustClaw if you want secure cloud actions, ZeroClaw if you want Rust speed, NanoClaw if you want container isolation, nanobot if you want a tiny readable codebase, and memU Bot if you want proactive memory that improves over time.
One line summary for each tool:
TrustClaw: Cloud agent rebuilt around OAuth + sandboxed execution with 1000+ tools, so you get actions without running risky stuff locally.
ZeroClaw: Rust framework built for speed with a <10ms startup, 3.4MB binary, and 22+ providers.
NanoClaw: Runs agents in real OS-level containers (Apple Container or Docker) so each chat stays isolated instead of sharing one process.
nanobot: A full agent in about ~4,000 LOC with a live line counter, plus MCP support, so tools plug in cleanly.
memU Bot: A proactive assistant built on memU’s memory engine, designed for long-running agents and lower context cost, with a simple email-download install flow.
Why OpenClaw alternatives?
OpenClaw is super powerful, no doubt, but it comes with two big headaches that you've probably already felt.
Security
Setup Friction
Security
When your agent can read files, run shell commands, and pull in third-party “skills,” you are basically giving it the keys to your machine. The skill marketplace has already turned into a real problem, with researchers finding hundreds of malicious skills.
If you are not auditing everything you install, it is easy to get yourself cooked. A full security coverage on it: OpenClaw: Security Nightmare Dressed Up as a Day Dream

Setup Friction
The “self-host it and wire up” path is fun if you like tinkering, but it is also where most people get stuck. You end up handling gateways, background services, tokens, and permission issues (most of the time).
And it's not that you're probably going to use all the features that come with the bloated app, just a few, for most people, so alternatives often could be a good choice.
Below are five OpenClaw alternatives that can cover the same ground, often with a smoother and more minimal experience, depending on what you’re building.
Best OpenClaw Alternatives to Consider
1. TrustClaw
ℹ️ Rebuilt from scratch on OpenClaw's idea with 20000+ tools, with a focus on security and ease of use.

TrustClaw is for those who like the idea of OpenClaw but don't want to hand over their passwords to the agent and run it locally.
It's built by the Composio team, and the pitch is basically: you get an agent that is available 24/7, capable of taking real actions across a vast number (500+) of apps, but the risky parts like credentials and code execution are handled in a more controlled way.
What makes it different?
OAuth-only auth: You connect apps the normal way (OAuth), so you don't paste API keys or passwords into config files.
Sandboxed execution by default: Every action runs in an isolated cloud environment that disappears when the task finishes. So you are not running “agent code” locally with your permissions.
Managed tool surface: Instead of pulling random community “skills” from a public registry, TrustClaw uses Composio’s managed integrations and tooling.
Audit trails + kill switch: It keeps a full audit log, and you can revoke access with one click if needed.
The last point is important because agent toolchains are a real security risk right now. These marketplaces, with just one random add-on, can trick you into running malware. This has already happened. Ref: OpenClaw’s AI ‘skill’ extensions are a security nightmare
The kind of prompts it’s built for
“Handle my customer complaints and log in Notion”
It finds the right tools, fetches emails, creates drafts, and writes Notion pages (using tools such as:
GMAIL_FETCH_EMAILS,GMAIL_CREATE_DRAFT,NOTION_CREATE_PAGE).“Pull all Reddit threads mentioning [competitor] from the last 3 months, analyze sentiment...”
“Summarize all Slack messages in #product-feedback from this week...”
Why it’s comparatively better (for most of you)
Set up in seconds (vs. 30 to 60 minutes of tunnels and local setup)
Encrypted credentials managed by Composio (vs. plaintext local config)
Remote sandbox (vs. local machine execution)
Managed tool surface (vs. unvetted public skill registry)
Action logs + one-click revocation (vs. digging through config files)
and no need for Mac Mini 🤷♂️
Quick start
Go to TrustClaw and hit Get Started.
Connect the apps you want (OAuth flow).
Give it a task in plain language, or schedule one to run while you are offline.
Here's a demo: 👇

It's that simple: now you have OpenClaw running completely in the cloud, with managed permissions and the tools you require.
2. ZeroClaw
ℹ️ Written in Rust, it runs even on $10 hardware with <5MB RAM.

ZeroClaw keeps the agent stack lean. Instead of a big local setup with lots of moving parts, you get a lightweight Rust binary that starts fast and runs comfortably on cheap hardware. If you care more about speed, stability, and low resource use, this one hits the sweet spot.
What makes it different?
Ultra lightweight: designed to keep CPU and RAM usage low.
Quick boot: fast startup, good for bots and always-on tasks.
Modular: swap models, memory, tools, and channels without rewriting everything.
Why pick it over OpenClaw?
You want something minimal and predictable.
You’re running on a small VPS / Raspberry Pi / home lab.
You don’t need a huge plugin marketplace; you need a tool that just runs.
Quick Start
git clone https://github.com/zeroclaw-labs/zeroclaw.git cd zeroclaw cargo build --release cargo install --path . --force # quick setup with openrouter zeroclaw onboard --api-key sk-... --provider openrouter # chat zeroclaw agent -m "Hello, ZeroClaw!"
Here's a quick architecture overview for those who care: 👇

3. NanoClaw
ℹ️ OpenClaw's alternative that runs entirely in a container for security.

NanoClaw is basically the same thing but runs completely isolated inside a Docker container. The whole idea is simple: keep the codebase small, and put the risky stuff (bash, file access, tools) inside an isolated container so it can only touch what you explicitly mount.
That's pretty much the idea of NanoClaw.
What makes it different?
Container isolation by default: runs in Apple Container (macOS) or Docker (macOS/Linux), with filesystem isolation.
Per-chat sandboxing: each group/chat can have its own memory and its own mounted filesystem, separated from others.
Built on Anthropic’s Agents SDK: it’s basically designed to work nicely with Claude’s agent tooling and Claude Code.
WhatsApp + scheduled jobs: message it from your phone, and set recurring tasks that ping you back.
Quick start
git clone https://github.com/gavrielc/nanoclaw.git cd
Then run /setup. Claude Code handles everything: dependencies, authentication, container setup, and service configuration.
Here's a quick demo: 👇

4. nanobot
ℹ️ Ultra lightweight AI assistant built with Python.

Nanobot, as the name suggests, is quite small. The core agent is about ~4,000 lines of code, and the repo even publishes a live count you can verify with their script. That is the whole vibe: small enough that you can actually read it, trust it, and change it.
What makes it different?
Core size metric: ~4,000 LOC, with a “real-time” line count shown in the README (and a script to verify).
MCP support (fresh): added 2026-02-14, so it can plug into MCP tool servers without you reinventing the plumbing.
Runs where you already are: built-in “gateway” mode supports a bunch of chat surfaces like Telegram, Discord, WhatsApp, Slack, Email, and more.
Quick Start
pip install nanobot-ai nanobot onboard nanobot agent # local interactive chat nanobot gateway # run it as a chat bot (Telegram, Discord, WhatsApp, etc)
Here's a quick architecture:

Here's a video to give you an idea of how it works: 👇

5. memU Bot
ℹ️ Built for 24/7 proactive agents designed for long-running use.

memU Bot is built for people who want an agent that keeps running and becomes more useful over time, instead of resetting to zero every time you open a new chat.
The site definitely looks like it was coded by a 12-year-old, but don’t let that scare you off, because the product underneath is really good.
Under the hood, it’s tied to memU, NevaMind’s memory framework for long-running proactive agents, with a focus on reducing long-run context cost by caching insights.
What makes it different?
Always-on + proactive: it’s designed to sit in the background and capture intent (not just respond to prompts).
Memory system that scales: memU treats memory like a file system (categories, memory items, cross-links), so the agent can fetch relevant fragments instead of shoving the whole history into every request.
Quick start
It's a bit more involved than other options.
If you just want the product (memU Bot):
Go to memu.bot, enter your email, and get the download link they send you.
Install it like a normal desktop app (they provide a macOS .dmg in the tutorial flow).
Start it, connect the channel you want (Telegram, etc.), and let it run so it can build memory over time.
git clone <https://github.com/NevaMind-AI/memU.git> cd memU # Requires Python 3.13+ pip install -e . # set your key (OpenAI is the default in their quick tests) export OPENAI_API_KEY="your_api_key" # quick test using in-memory storage cd
Want persistent memory backed by Postgres + pgvector?
docker run -d \ --name memu-postgres \ -e POSTGRES_USER=postgres \ -e POSTGRES_PASSWORD=postgres \ -e POSTGRES_DB=memu \ -p 5432:5432 \ pgvector/pgvector:pg16 export OPENAI_API_KEY="your_api_key" cd
They also provide a small runnable "proactive loop" example if you want to see the behaviour without going through tests:
cd
There's also a Cloud version you can try.

That concludes this article. Thank you so much for reading! 🫡
Frequently Asked Questions
What’s the simplest OpenClaw alternative if I just want things to work fast?
If you want the least setup pain, TrustClaw is the most “plug in and go” because it’s cloud-hosted, uses OAuth, and handles execution plus permissions for you. If you want something lightweight you can run yourself, ZeroClaw is the fastest path to a minimal local agent.
Which option is best if I’m mainly worried about security?
Two strong directions: TrustClaw if you want cloud sandboxing, OAuth-only auth, audit logs, and quick revocation, or NanoClaw if you prefer hard isolation via real containers where the agent only touches what you mount. If you’re worried about sketchy skill marketplaces, both avoid the “install random skills” trap in different ways.
I want something minimal and hackable. What should I pick?
Go with nanobot if you want a small, readable codebase you can actually modify without getting lost, plus MCP support for plugging in tools cleanly. ZeroClaw is also minimal, but it’s optimized more for performance and stability than “read the whole repo in a weekend.”
Which one makes the most sense for long-running agents that improve over time?
That’s memU Bot. It’s built around proactive memory so it can get more useful as it runs, while keeping context costs down by retrieving only relevant memory instead of replaying entire chat history.
Recommended Blogs
Recommended Blogs

Connect AI agents to SaaS apps in Minutes
Connect AI agents to SaaS apps in Minutes
We handle auth, tools, triggers, and logs, so you build what matters.
Stay updated.

Stay updated.


