AI agent authentication platforms: buyer's guide and comparison (2026)
AI agent authentication platforms: buyer's guide and comparison (2026)
You've built a prototype agent that shows real promise. It can reason, plan, and even execute simple tasks. But now you've hit the wall that separates demos from production: connecting your agent securely and reliably to the real-world tools your users depend on.
End-user authentication keeps blocking teams from shipping production-grade agents. Managing OAuth flows, credential storage, and token refreshes is honestly a pain, and it's not where you want to spend your engineering time.
This guide gives you a framework for evaluating and selecting an AI agent authentication platform. So you can focus on your agent's core logic, not the plumbing.
TL;DR: Top AI agent authentication platforms
What it is: An AI agent authentication platform is middleware that brokers end-user OAuth and API access, keeping sensitive tokens out of the agent runtime.
Evaluation criteria: Security and compliance, developer experience (DX), end-user experience (UX), scalability and reliability, and total cost of ownership (TCO).
Decision shortcuts: Choose Composio for developer-first speed, Merge for enterprise governance, Nango for open-source flexibility, and Arcade for just-in-time permissions.
Key caution: Self-hosting an open-source solution shifts the operational burden onto your team. Security, compliance (SOC 2, GDPR), and vault maintenance become your problem.
Platform | Best for | Key differentiator |
|---|---|---|
Composio | Developer-first teams building production agents | Unified SDK, managed auth, & dev tooling |
Merge | Teams needing deep governance and access controls | "Tool Packs" and rule-based policies |
Nango | Teams prioritizing open-source and broad API coverage | Open-source core with a large connector library |
Arcade | Use cases requiring just-in-time permission checks | Task-time permission verification |
How to evaluate an AI agent authentication platform: the 6 pillars
Choosing an authentication platform is a foundational architectural decision. Don't just compare connector counts. Use this framework to evaluate what actually matters for production systems.
Security & Compliance: Security goes way beyond checking the "OAuth" box. A production-ready platform needs a secure credential vault with encryption at rest, automated token lifecycle management (refresh, rotation, and revocation), detailed audit logs for every action, and verifiable compliance with standards like SOC 2 and GDPR.
Developer Experience (DX): How fast can your team ship a secure, reliable integration? Look at SDK quality, CLI tools for local testing, and documentation clarity. Great DX means your devs spend time on agent logic, not wrestling with auth complexity.
End-User Experience (UX): Your users need to connect their accounts without friction. Look for a single, unified, customizable (white-label) UI that handles each app's unique authentication flow behind the scenes and presents a simple, consistent experience.
Scalability & Reliability: Can the platform handle thousands of concurrent connections without falling over? It needs to proactively refresh tokens before they expire, monitor for broken connections, and alert you when things go wrong. Ask about uptime SLAs.
Business Model & Total Cost of Ownership (TCO): Look beyond the sticker price. Is pricing per-connection, per-user, or usage-based? And if you're considering self-hosting open-source, factor in the real costs: engineering time for maintenance, security hardening, and compliance work.
Migration readiness: Even if you love a platform today, plan for change. Migration readiness helps you avoid a disruptive "everyone reconnect now" moment if pricing, requirements, or vendor strategy shifts. Before committing, confirm three things:
OAuth app control: Can you keep control of OAuth apps and callback URLs where needed?
Connection continuity: Can you manage connections to support a phased cutover (dual-running) during migration?
Re-auth minimization: If you switch providers, can you migrate without forcing every user to reconnect on day one?
AI agent authentication platforms comparison (2026)
Feature comparison matrix
Feature | Composio | Merge | Nango | Arcade |
|---|---|---|---|---|
Unified SDK/Framework | ✅ | ✅ | ✅ | 🟡 Ecosystem and framework coverage are still maturing |
Managed credential vault | ✅ | ✅ | 🟡 Cloud is managed; self-host shifts compliance/ops to you. | ✅ |
White-Label UI | ✅ | ✅ | ✅ | 🟡 Customization and the breadth of supported flows are limited |
CLI for auth + integration local testing | ✅ | 🟡 Limited CLI functionality for configuration | ✅ | ❌ |
Automated token refresh | ✅ | ✅ | ✅ | ✅ |
Granular scopes | ✅ | ✅ | ✅ | ✅ |
Audit logs | ✅ | ✅ | ✅ | ✅ |
Agent framework integrations | ✅ | ✅ | 🟡 Native, ready-made bindings across major agent frameworks are still developing. | 🟡 Native, ready-made bindings across major agent frameworks are still developing. |
End-user setup guides | ✅ | ✅ | ✅ | 🟡 Basic docs exist but lack the depth of polished, step-by-step guides. |
Migration readiness | ✅ | 🟡 Depends on enterprise controls & migration workflow | ✅ | 🟡 Depends on tool/runtime deployment model |
Note: 🟡 indicates partial or developing support.
Composio overview
Best for: Developer-first teams who need to move fast without compromising on security or user experience.
Composio accelerates agent development from the ground up. It pairs a managed auth platform with powerful, code-centric tools.
Security: Provides a fully managed, SOC 2-compliant platform and automated token lifecycle management. Credentials never reach your agent's context.
Developer Experience: This is really where Composio shines. The unified SDK abstracts every integration into a consistent interface. Paired with a powerful CLI for local development and testing, you can build and debug complex agentic workflows entirely on your local machine before deploying. Teams often report cutting go-to-market time by 90%.
End-User Experience: Provides a customizable connection flow UI that your product can embed. Users can securely connect and manage their accounts across supported applications without leaving your interface.
Scalability: Runs on a serverless architecture designed for high-throughput, spiky workloads typical of AI agents.
Business Model & TCO: Features transparent, usage-based pricing that scales with your agent's adoption—no surprise platform fees.
Migration readiness: Composio is optimized for managed reliability and speed; if you ever need to migrate, plan a staged cutover to minimize user re-auth and avoid disruption.
Merge overview
Best for: Enterprise teams that need strong, centralized governance and policy enforcement for tool usage.
Merge works well when security administrators and compliance officers need granular control over how AI agents interact with company data.
Security: This is Merge's core focus. Its "Tool Packs" and rule-based policies let administrators precisely define which data agents can access and what actions they can perform. Critical for regulated industries.
Developer Experience: The experience leans toward configuration in the Merge admin UI rather than pure code-first. This can powerfully enforce policies but may feel restrictive if you're building highly dynamic agent logic directly in code.
Business Model & TCO: Merge prices for enterprises. It may be less accessible for early-stage startups or teams scaling from zero.
Nango overview
Best for: Teams who strongly prefer open-source and need the broadest possible range of API integrations.
Nango is a powerful open-source tool that gives teams maximum control over their integration infrastructure.
Security: When self-hosted, your team bears full responsibility for the credential vault's security and compliance burden (SOC 2, GDPR). You'll need dedicated security and infrastructure expertise.
Developer Experience: The open-source model gives you ultimate extensibility. You can build custom connectors. But that flexibility comes with real operational overhead: hosting, maintaining, and updating the platform yourself.
Integration Support: Its community-driven model has produced a large library of connectors.
Business Model & TCO: The core software is free, but the TCO runs high. Factor in ongoing engineering and cloud infrastructure costs for hosting, security hardening, maintenance, and compliance certifications.
Arcade overview
Best for: Applications that require fine-grained, just-in-time permissioning at the moment a task executes.
Arcade is a newer player with a unique focus on task-time authorization. It's well-suited for human-in-the-loop workflows.
Security: Verifying permissions just-in-time before an action executes adds an extra safety layer, especially when actions need user confirmation.
Developer Experience: As a more recent entrant, its tooling ecosystem and prebuilt integrations lag behind those of established competitors.
Business Model & TCO: Teams should evaluate the pricing model for long-term predictability as the platform evolves.
Reference architecture: how AI agent authentication works in production
An AI agent authentication platform is a critical middleware that sits between your agent and the outside world. It acts as a secure gatekeeper for all third-party actions.
Here's how the process works:
Your AI Agent Application determines that a user-requested action is needed (e.g., "create a ticket in Jira").
Instead of handling the API call itself, the application calls a function in the Auth Platform's SDK (e.g.,
composio.jira.create_issue(...)).The Auth Platform retrieves the correct, securely stored user token from its vault, verifies that it is still valid (refreshing if needed), and executes the request against the Third-Party API.
The SDK passes the result back to your agent.
This brokered pattern means sensitive credentials, such as OAuth tokens, never reach your application's runtime. That dramatically reduces your security exposure.
Typical Flow:
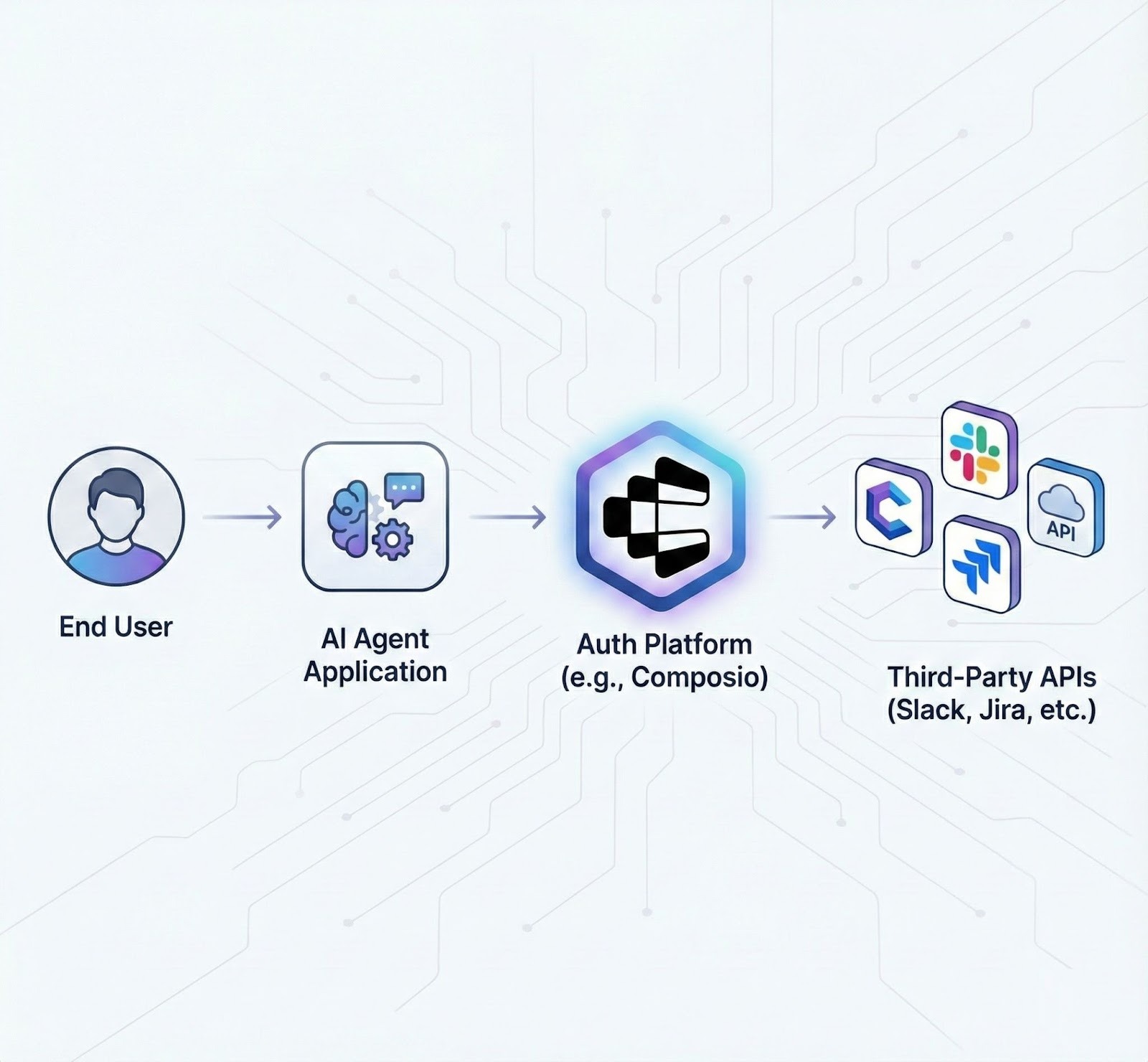
How to choose the right AI agent authentication platform
Selecting an AI agent authentication platform means choosing a foundational partner for security, developer velocity, and user trust. It's more than just connecting APIs.
The decision comes down to a key trade-off: do you need strict, top-down governance (Merge), ultimate flexibility with open-source (Nango), or developer-first speed with managed security (Composio)?
Choose the foundation that aligns with your team's priorities and technical DNA.
Ready to build production-grade agents without the auth headache? Explore Composio's unified framework or talk to one of our integration experts.
Frequently Asked Questions
Do I need an agent auth platform, or should I build OAuth and token storage myself?
Use a platform if you need production security, auditability, and reliability quickly. Build it yourself only if you can own a secure vault, refresh logic, and monitor and comply with it long-term.
Where are user tokens stored, and do tokens ever reach the agent/LLM context?
In a secure credential vault. The agent should only request actions via an SDK/API. Tokens should never reach prompts, logs, or the LLM context.
How do agent auth platforms support multi-tenant, per-user connections?
They map each end user (and workspace/org) to separate OAuth connections and scopes, so actions execute with the correct user identity and permissions.
What compliance and security features should I require (SOC 2, GDPR, audit logs)?
At minimum: encryption at rest, key management, token rotation/refresh, revocation, audit logs, and SOC 2. Add GDPR/HIPAA requirements based on your data and customers.
How does an auth platform reduce agent failures in production?
By proactively refreshing tokens, detecting broken connections, and providing retries/monitoring. Your agent actions don't fail due to expired credentials or auth drift.
What pricing models are common for agent authentication platforms?
Typically per connection, per active user, or usage-based (API calls/actions). Total cost should include operational overhead if you self-host.
How do these platforms integrate with agent frameworks (LangChain, CrewAI, OpenAI Assistants)?
Usually via SDKs/tools that expose authenticated actions as callable functions. Agent frameworks like LangChain and CrewAI can invoke tools without implementing OAuth flows themselves.
How should AI agents handle OAuth token refresh?
Token refresh should be completely invisible and automatic. A dedicated authentication platform handles refreshes in the background, proactively obtaining new access tokens before the old ones expire. Managed platforms include this as a core feature.
Which is more secure for AI agents: API keys or OAuth?
For actions performed on behalf of an end-user, OAuth is far superior. OAuth provides user-specific, revocable, and narrowly-scoped permissions, adhering to the principle of least privilege. Static API keys work for system-to-system integrations where a single, shared identity is fine. But they provide less security for delegated user access.
How do you store AI agent credentials securely (token vault)?
Building a custom, compliant (e.g., SOC 2 Type II) token vault is a significant engineering project involving complex encryption, key management, and audit trails. Industry best practice: delegate this to a managed platform that provides a secure, audited vault out of the box. You'll save months of development and compliance effort.
You've built a prototype agent that shows real promise. It can reason, plan, and even execute simple tasks. But now you've hit the wall that separates demos from production: connecting your agent securely and reliably to the real-world tools your users depend on.
End-user authentication keeps blocking teams from shipping production-grade agents. Managing OAuth flows, credential storage, and token refreshes is honestly a pain, and it's not where you want to spend your engineering time.
This guide gives you a framework for evaluating and selecting an AI agent authentication platform. So you can focus on your agent's core logic, not the plumbing.
TL;DR: Top AI agent authentication platforms
What it is: An AI agent authentication platform is middleware that brokers end-user OAuth and API access, keeping sensitive tokens out of the agent runtime.
Evaluation criteria: Security and compliance, developer experience (DX), end-user experience (UX), scalability and reliability, and total cost of ownership (TCO).
Decision shortcuts: Choose Composio for developer-first speed, Merge for enterprise governance, Nango for open-source flexibility, and Arcade for just-in-time permissions.
Key caution: Self-hosting an open-source solution shifts the operational burden onto your team. Security, compliance (SOC 2, GDPR), and vault maintenance become your problem.
Platform | Best for | Key differentiator |
|---|---|---|
Composio | Developer-first teams building production agents | Unified SDK, managed auth, & dev tooling |
Merge | Teams needing deep governance and access controls | "Tool Packs" and rule-based policies |
Nango | Teams prioritizing open-source and broad API coverage | Open-source core with a large connector library |
Arcade | Use cases requiring just-in-time permission checks | Task-time permission verification |
How to evaluate an AI agent authentication platform: the 6 pillars
Choosing an authentication platform is a foundational architectural decision. Don't just compare connector counts. Use this framework to evaluate what actually matters for production systems.
Security & Compliance: Security goes way beyond checking the "OAuth" box. A production-ready platform needs a secure credential vault with encryption at rest, automated token lifecycle management (refresh, rotation, and revocation), detailed audit logs for every action, and verifiable compliance with standards like SOC 2 and GDPR.
Developer Experience (DX): How fast can your team ship a secure, reliable integration? Look at SDK quality, CLI tools for local testing, and documentation clarity. Great DX means your devs spend time on agent logic, not wrestling with auth complexity.
End-User Experience (UX): Your users need to connect their accounts without friction. Look for a single, unified, customizable (white-label) UI that handles each app's unique authentication flow behind the scenes and presents a simple, consistent experience.
Scalability & Reliability: Can the platform handle thousands of concurrent connections without falling over? It needs to proactively refresh tokens before they expire, monitor for broken connections, and alert you when things go wrong. Ask about uptime SLAs.
Business Model & Total Cost of Ownership (TCO): Look beyond the sticker price. Is pricing per-connection, per-user, or usage-based? And if you're considering self-hosting open-source, factor in the real costs: engineering time for maintenance, security hardening, and compliance work.
Migration readiness: Even if you love a platform today, plan for change. Migration readiness helps you avoid a disruptive "everyone reconnect now" moment if pricing, requirements, or vendor strategy shifts. Before committing, confirm three things:
OAuth app control: Can you keep control of OAuth apps and callback URLs where needed?
Connection continuity: Can you manage connections to support a phased cutover (dual-running) during migration?
Re-auth minimization: If you switch providers, can you migrate without forcing every user to reconnect on day one?
AI agent authentication platforms comparison (2026)
Feature comparison matrix
Feature | Composio | Merge | Nango | Arcade |
|---|---|---|---|---|
Unified SDK/Framework | ✅ | ✅ | ✅ | 🟡 Ecosystem and framework coverage are still maturing |
Managed credential vault | ✅ | ✅ | 🟡 Cloud is managed; self-host shifts compliance/ops to you. | ✅ |
White-Label UI | ✅ | ✅ | ✅ | 🟡 Customization and the breadth of supported flows are limited |
CLI for auth + integration local testing | ✅ | 🟡 Limited CLI functionality for configuration | ✅ | ❌ |
Automated token refresh | ✅ | ✅ | ✅ | ✅ |
Granular scopes | ✅ | ✅ | ✅ | ✅ |
Audit logs | ✅ | ✅ | ✅ | ✅ |
Agent framework integrations | ✅ | ✅ | 🟡 Native, ready-made bindings across major agent frameworks are still developing. | 🟡 Native, ready-made bindings across major agent frameworks are still developing. |
End-user setup guides | ✅ | ✅ | ✅ | 🟡 Basic docs exist but lack the depth of polished, step-by-step guides. |
Migration readiness | ✅ | 🟡 Depends on enterprise controls & migration workflow | ✅ | 🟡 Depends on tool/runtime deployment model |
Note: 🟡 indicates partial or developing support.
Composio overview
Best for: Developer-first teams who need to move fast without compromising on security or user experience.
Composio accelerates agent development from the ground up. It pairs a managed auth platform with powerful, code-centric tools.
Security: Provides a fully managed, SOC 2-compliant platform and automated token lifecycle management. Credentials never reach your agent's context.
Developer Experience: This is really where Composio shines. The unified SDK abstracts every integration into a consistent interface. Paired with a powerful CLI for local development and testing, you can build and debug complex agentic workflows entirely on your local machine before deploying. Teams often report cutting go-to-market time by 90%.
End-User Experience: Provides a customizable connection flow UI that your product can embed. Users can securely connect and manage their accounts across supported applications without leaving your interface.
Scalability: Runs on a serverless architecture designed for high-throughput, spiky workloads typical of AI agents.
Business Model & TCO: Features transparent, usage-based pricing that scales with your agent's adoption—no surprise platform fees.
Migration readiness: Composio is optimized for managed reliability and speed; if you ever need to migrate, plan a staged cutover to minimize user re-auth and avoid disruption.
Merge overview
Best for: Enterprise teams that need strong, centralized governance and policy enforcement for tool usage.
Merge works well when security administrators and compliance officers need granular control over how AI agents interact with company data.
Security: This is Merge's core focus. Its "Tool Packs" and rule-based policies let administrators precisely define which data agents can access and what actions they can perform. Critical for regulated industries.
Developer Experience: The experience leans toward configuration in the Merge admin UI rather than pure code-first. This can powerfully enforce policies but may feel restrictive if you're building highly dynamic agent logic directly in code.
Business Model & TCO: Merge prices for enterprises. It may be less accessible for early-stage startups or teams scaling from zero.
Nango overview
Best for: Teams who strongly prefer open-source and need the broadest possible range of API integrations.
Nango is a powerful open-source tool that gives teams maximum control over their integration infrastructure.
Security: When self-hosted, your team bears full responsibility for the credential vault's security and compliance burden (SOC 2, GDPR). You'll need dedicated security and infrastructure expertise.
Developer Experience: The open-source model gives you ultimate extensibility. You can build custom connectors. But that flexibility comes with real operational overhead: hosting, maintaining, and updating the platform yourself.
Integration Support: Its community-driven model has produced a large library of connectors.
Business Model & TCO: The core software is free, but the TCO runs high. Factor in ongoing engineering and cloud infrastructure costs for hosting, security hardening, maintenance, and compliance certifications.
Arcade overview
Best for: Applications that require fine-grained, just-in-time permissioning at the moment a task executes.
Arcade is a newer player with a unique focus on task-time authorization. It's well-suited for human-in-the-loop workflows.
Security: Verifying permissions just-in-time before an action executes adds an extra safety layer, especially when actions need user confirmation.
Developer Experience: As a more recent entrant, its tooling ecosystem and prebuilt integrations lag behind those of established competitors.
Business Model & TCO: Teams should evaluate the pricing model for long-term predictability as the platform evolves.
Reference architecture: how AI agent authentication works in production
An AI agent authentication platform is a critical middleware that sits between your agent and the outside world. It acts as a secure gatekeeper for all third-party actions.
Here's how the process works:
Your AI Agent Application determines that a user-requested action is needed (e.g., "create a ticket in Jira").
Instead of handling the API call itself, the application calls a function in the Auth Platform's SDK (e.g.,
composio.jira.create_issue(...)).The Auth Platform retrieves the correct, securely stored user token from its vault, verifies that it is still valid (refreshing if needed), and executes the request against the Third-Party API.
The SDK passes the result back to your agent.
This brokered pattern means sensitive credentials, such as OAuth tokens, never reach your application's runtime. That dramatically reduces your security exposure.
Typical Flow:

How to choose the right AI agent authentication platform
Selecting an AI agent authentication platform means choosing a foundational partner for security, developer velocity, and user trust. It's more than just connecting APIs.
The decision comes down to a key trade-off: do you need strict, top-down governance (Merge), ultimate flexibility with open-source (Nango), or developer-first speed with managed security (Composio)?
Choose the foundation that aligns with your team's priorities and technical DNA.
Ready to build production-grade agents without the auth headache? Explore Composio's unified framework or talk to one of our integration experts.
Frequently Asked Questions
Do I need an agent auth platform, or should I build OAuth and token storage myself?
Use a platform if you need production security, auditability, and reliability quickly. Build it yourself only if you can own a secure vault, refresh logic, and monitor and comply with it long-term.
Where are user tokens stored, and do tokens ever reach the agent/LLM context?
In a secure credential vault. The agent should only request actions via an SDK/API. Tokens should never reach prompts, logs, or the LLM context.
How do agent auth platforms support multi-tenant, per-user connections?
They map each end user (and workspace/org) to separate OAuth connections and scopes, so actions execute with the correct user identity and permissions.
What compliance and security features should I require (SOC 2, GDPR, audit logs)?
At minimum: encryption at rest, key management, token rotation/refresh, revocation, audit logs, and SOC 2. Add GDPR/HIPAA requirements based on your data and customers.
How does an auth platform reduce agent failures in production?
By proactively refreshing tokens, detecting broken connections, and providing retries/monitoring. Your agent actions don't fail due to expired credentials or auth drift.
What pricing models are common for agent authentication platforms?
Typically per connection, per active user, or usage-based (API calls/actions). Total cost should include operational overhead if you self-host.
How do these platforms integrate with agent frameworks (LangChain, CrewAI, OpenAI Assistants)?
Usually via SDKs/tools that expose authenticated actions as callable functions. Agent frameworks like LangChain and CrewAI can invoke tools without implementing OAuth flows themselves.
How should AI agents handle OAuth token refresh?
Token refresh should be completely invisible and automatic. A dedicated authentication platform handles refreshes in the background, proactively obtaining new access tokens before the old ones expire. Managed platforms include this as a core feature.
Which is more secure for AI agents: API keys or OAuth?
For actions performed on behalf of an end-user, OAuth is far superior. OAuth provides user-specific, revocable, and narrowly-scoped permissions, adhering to the principle of least privilege. Static API keys work for system-to-system integrations where a single, shared identity is fine. But they provide less security for delegated user access.
How do you store AI agent credentials securely (token vault)?
Building a custom, compliant (e.g., SOC 2 Type II) token vault is a significant engineering project involving complex encryption, key management, and audit trails. Industry best practice: delegate this to a managed platform that provides a secure, audited vault out of the box. You'll save months of development and compliance effort.
Recommended Blogs
Recommended Blogs

Connect AI agents to SaaS apps in Minutes
Connect AI agents to SaaS apps in Minutes
We handle auth, tools, triggers, and logs, so you build what matters.
Stay updated.

Stay updated.


