How to create OAuth2 credentials for Microsoft Apps (Outlook)
How to create OAuth2 credentials for Microsoft Apps (Outlook)
In this guide, I’ll walk through the process of setting up OAuth for Microsoft Outlook using the Azure App Registrations portal.
This lets your app connect securely to Microsoft Graph APIs (which power Outlook, OneDrive, Teams, etc.).
Note: You do not need a Microsoft 365 Developer sandbox for this. A free Microsoft personal account is enough to register an OAuth app.
Step 1: Create an Azure App Registration
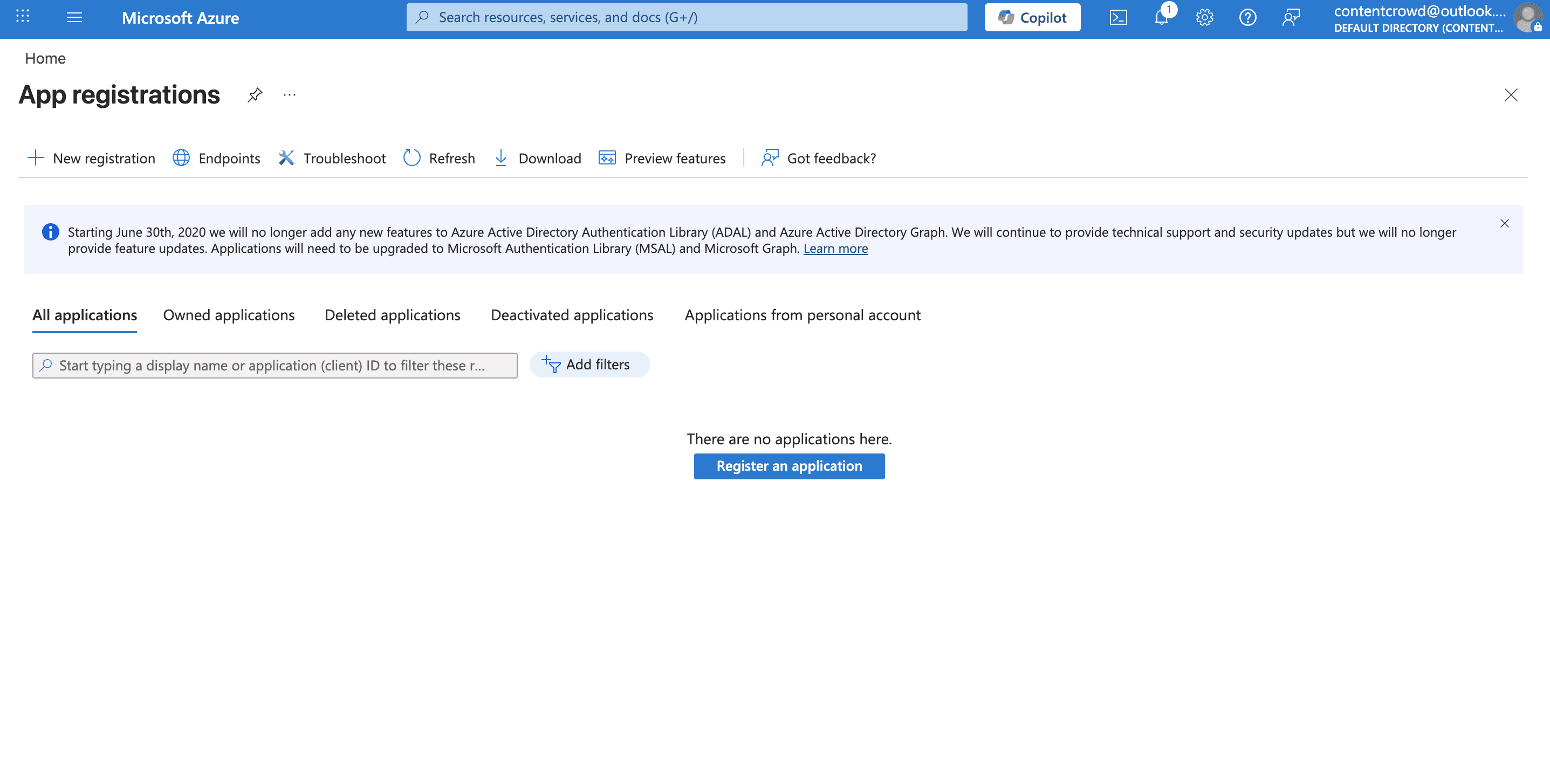
Go to the Azure Portal.
In the search bar, search for App registrations and click + New registration.
Fill in your app details:
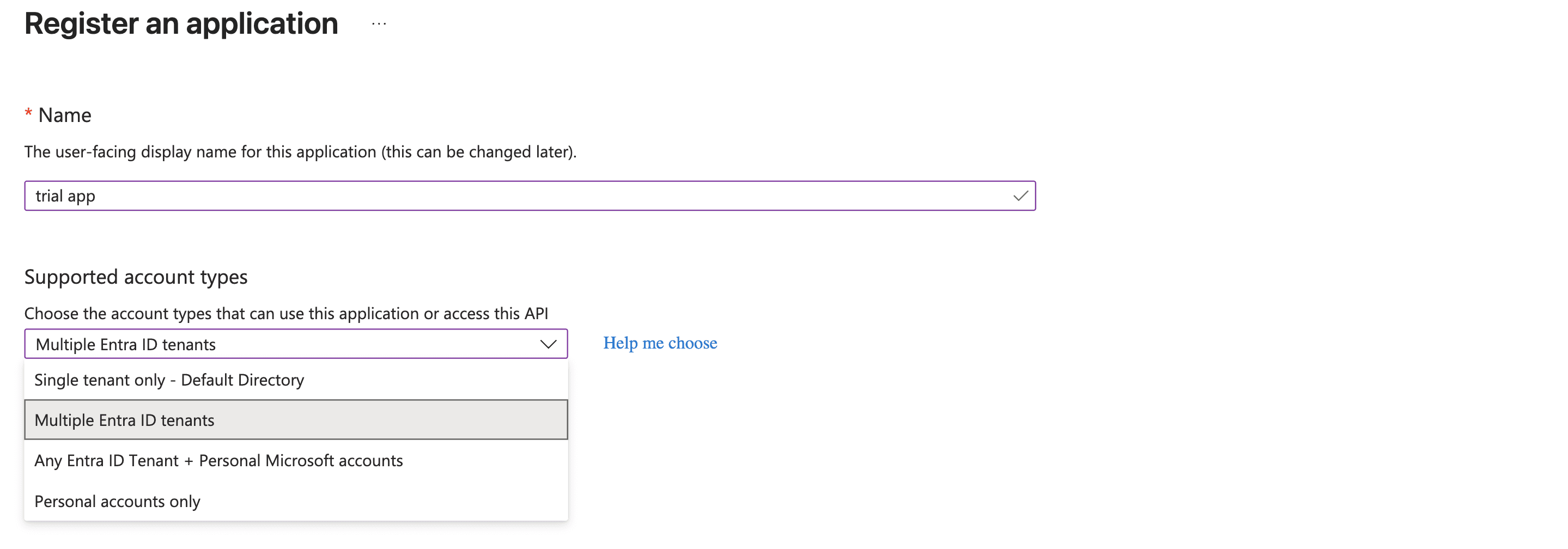
Name: Example →
Outlook IntegrationSupported account types:
Choose based on your needs:
If only your organisation would use it → Single tenant only
If multiple organisations need access → Multiple Entra ID tenants -> Allow all tenants or Allow only certain tenants (Check the Additional section for restricting access specific tenants)
If you need personal Outlook accounts too → Any Entra ID Tenant + Personal Microsoft accounts.
Redirect URI (optional): Choose Web and paste:
Click Register.
Step 2: Generate Client Credentials
Once your app is created, you’ll be redirected to its Overview page.
Copy the Application (client) ID — this is your Client ID.
From the sidebar, go to Certificates & secrets → + New client secret.
Add a description and set expiry (6 or 12 months recommended).
Copy the generated Client Secret and save it securely.

⚠️ Important: You won’t be able to see the secret again once you leave the page.
Step 3: Configure API Permissions
Now, we’ll grant the app access to Outlook data.
In the sidebar, click API Permissions → + Add a permission.
Select Microsoft Graph.
Choose Delegated permissions.
Add the required common Outlook-related scopes, such as:
Mail.Read→ Read users’ emailsMail.Send→ Send emails on behalf of the useroffline_access→ Enable refresh tokensopenid profile email→ Basic login profile
For other apps like Teams, SharePoint, Excel, etc add specific permissions
Click on Grant Admin Consent to authorise the app to call APIs.

Click Add permissions.
Step 4: Update Redirect URIs
From the sidebar, open Authentication.
Under Redirect URIs, make sure this URL is added:
Under Advanced settings, enable Allow public client flows (this makes it easier to test).
Save changes.
Step 5: Create the Auth Config in Composio
With your Client ID and Client Secret ready, head over to the Composio Dashboard.
Click Create Auth Config.

Select Microsoft Tenant (or Microsoft Teams if listed).
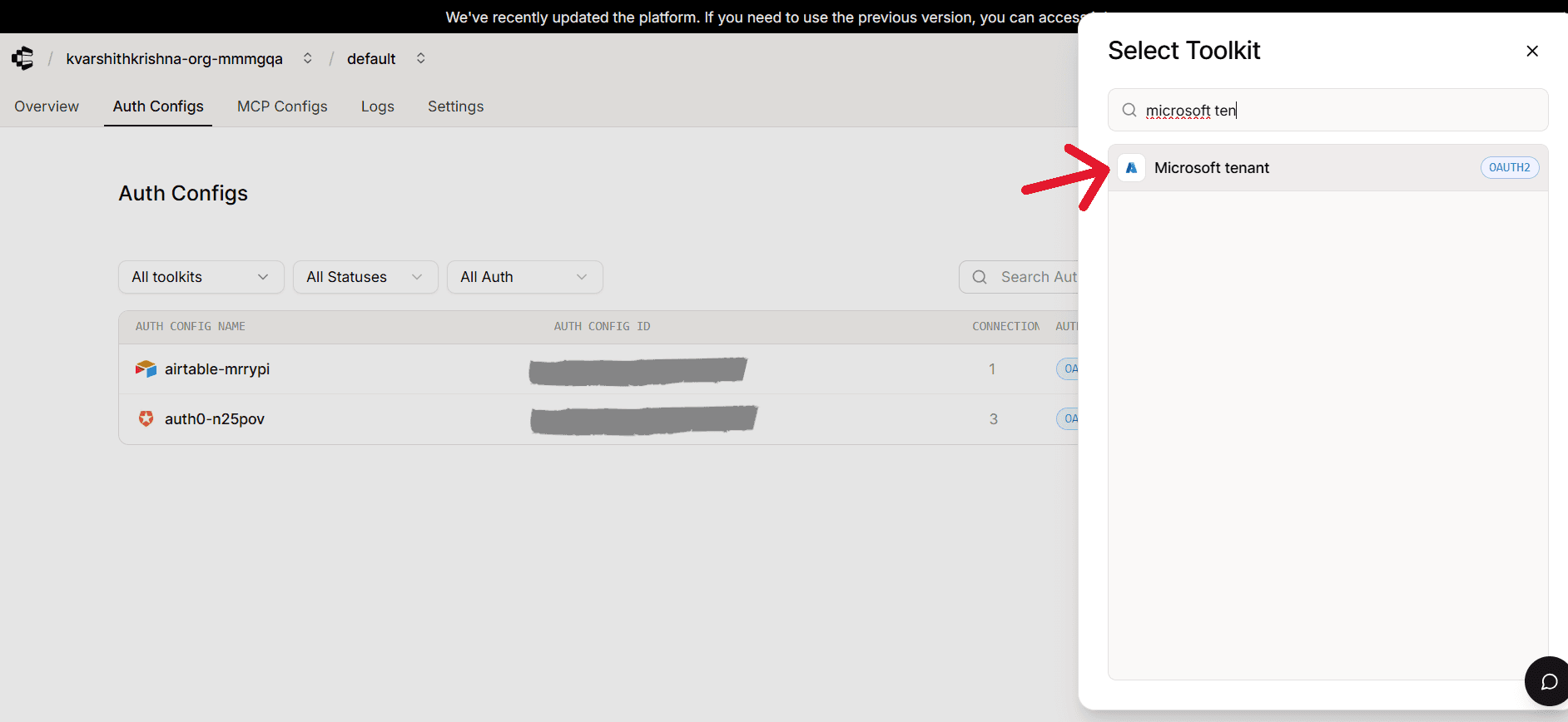
Choose OAuth2 as the authentication type.
Check Use your own developer authentication.
Paste in your:
Client ID → from Azure App Registration
Client Secret → from Certificates & secrets
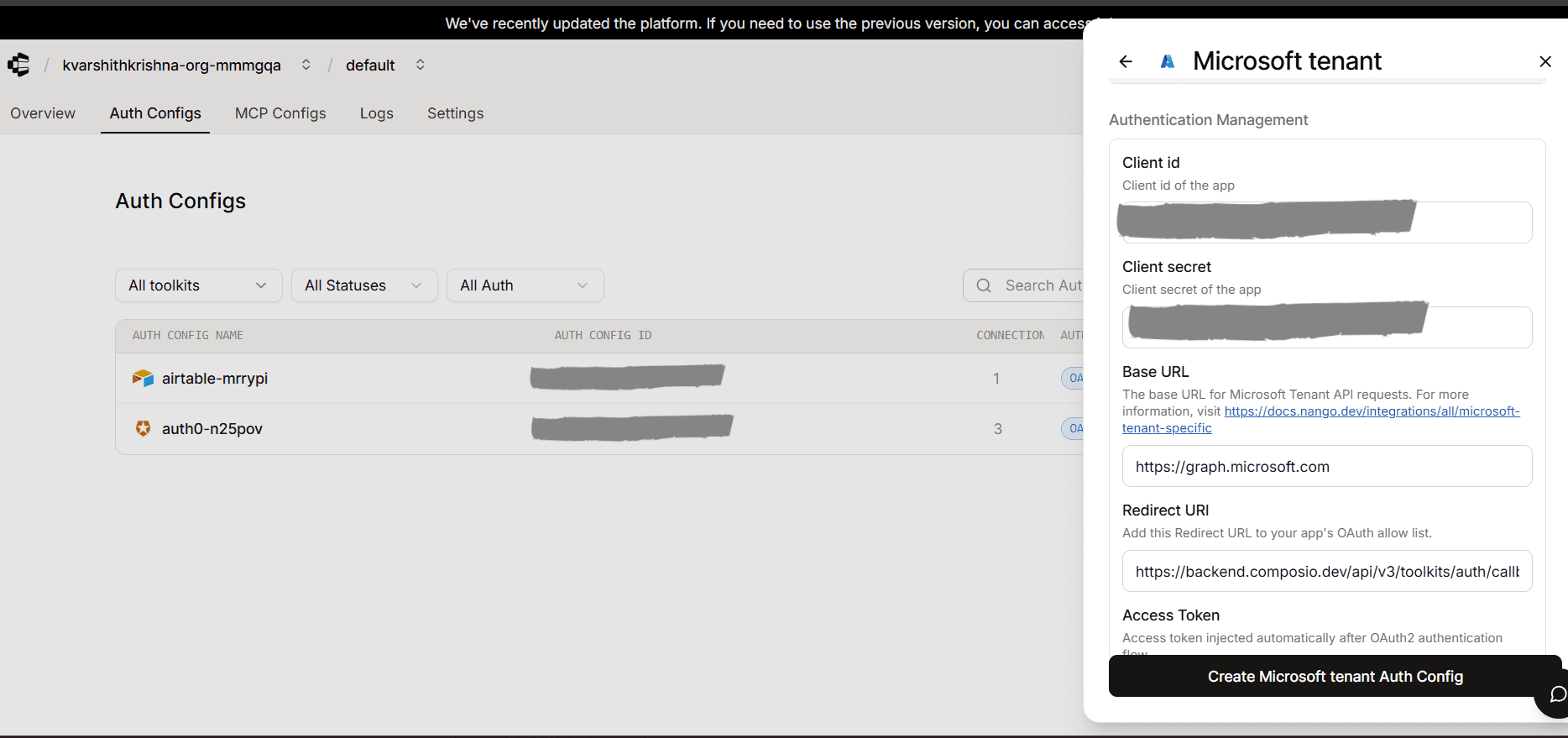
Redirect URI →
Save the config.
Step 6: Authorize and Connect
In Composio, click Connect Account for the Outlook config.
You’ll be redirected to Microsoft’s login screen.
Approve the requested permissions (Mail.Read, Mail.Send, etc.).
Composio stores the tokens once authorization succeeds.
API Base URL
For Microsoft Graph (which powers Outlook), the base URL is:
Example endpoints:
List user emails →
/me/messagesSend email →
/me/sendMail
Once done, copy the auth config ID (which starts with ac_) and use it in your application code via a secret manager.
Scopes for Other Microsoft Apps
If you want to integrate with other Microsoft services, you can reuse the same Azure app. Just add the required scopes in both Azure and Composio:
OneDrive →
Files.ReadWrite,Files.read.allTeams →
Channel.ReadWrite.AllSharepoint →
List.ReadExcel →
Files.ReadWrite
Once scopes are added, you can configure additional auth configs in Composio for each service.
Additional: Restricting Access to Specific Tenants
If you're using your own custom OAuth app and want to limit access to only your organization's tenant or specific customer tenants, follow the steps below.
When the OAuth app is set to Multiple Entra ID tenants, it uses the /common endpoint, which means any Microsoft organisation could potentially authenticate. To restrict this, you can use the Allowed tenants setting to whitelist only specific organisations.
Step 1: Set Supported Account Type
Go to portal.azure.com and navigate to your app registration.
In the search bar, search for App registrations and click + New registration.

In the following page, you will be asked add your App name and Authentication type.
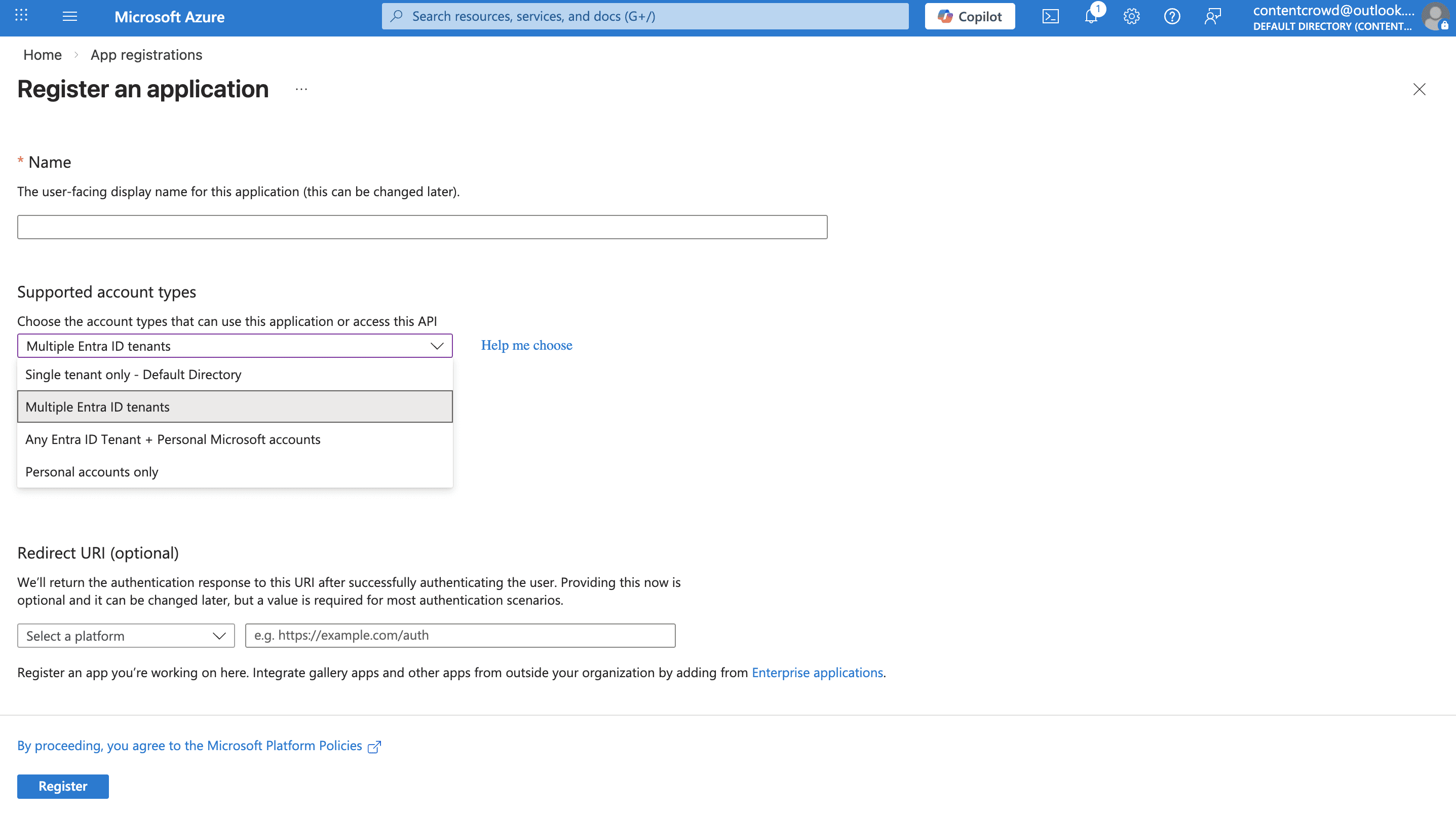
Under Authentication, click the Supported account types tab.
Select Multiple Entra ID tenants.

Step 2: Restrict to Specific Tenants
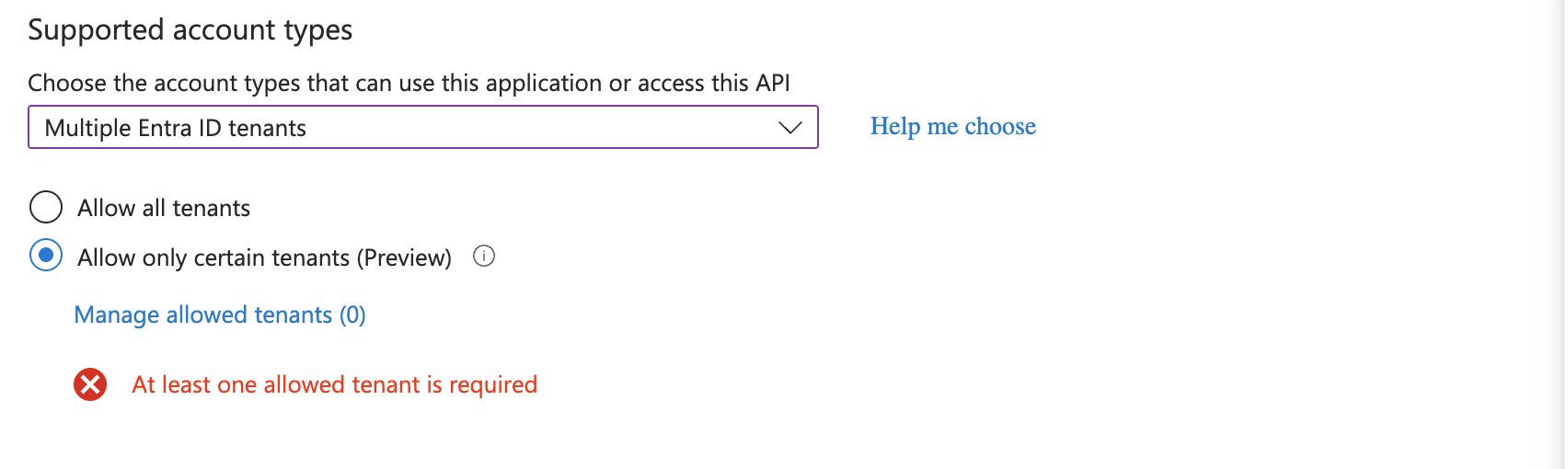
Under the Supported accounts tab, select "Allow only certain tenants (Preview)".
Click Manage allowed tenants.
Add the Tenant ID of each organisation you want to allow.
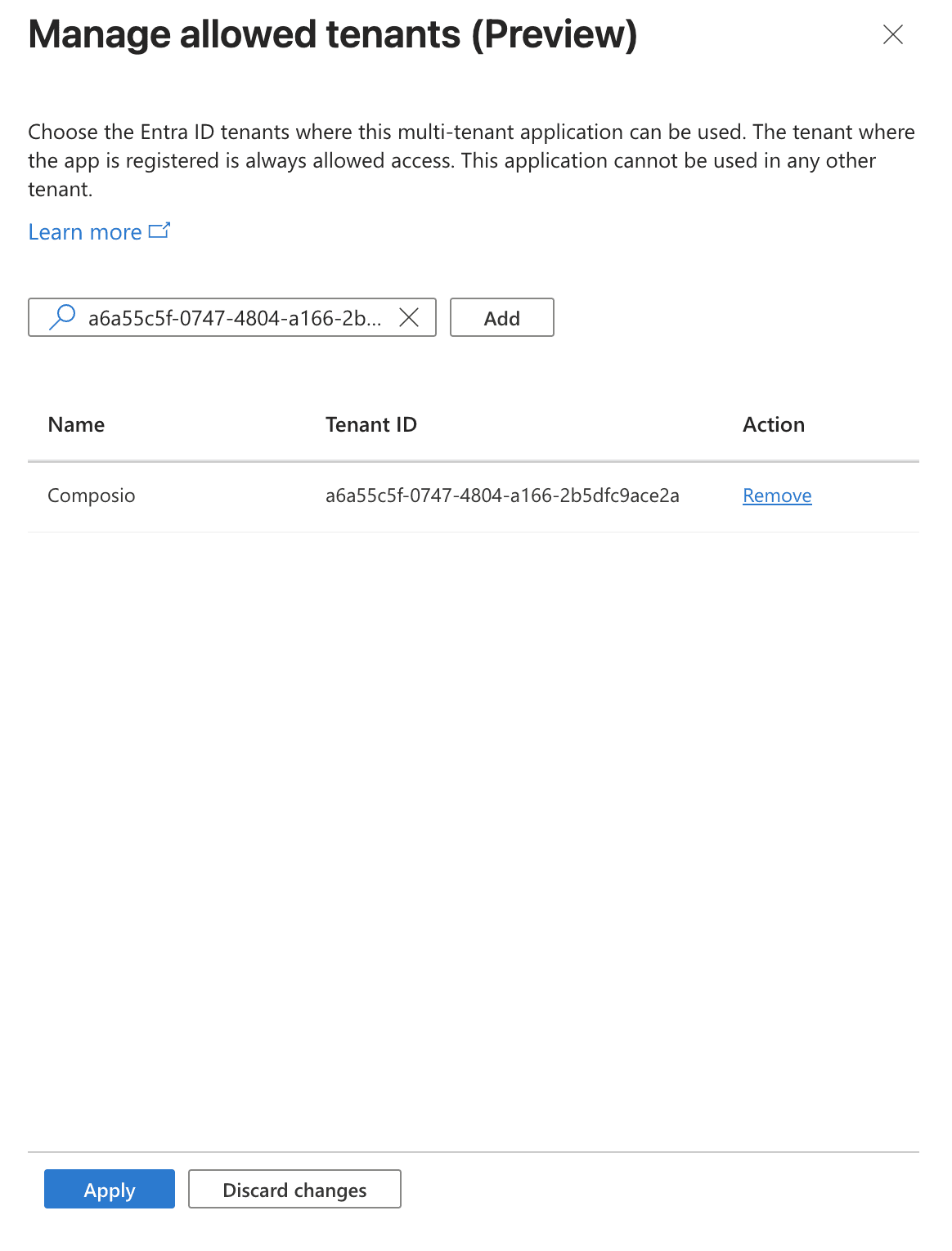
Click Apply.
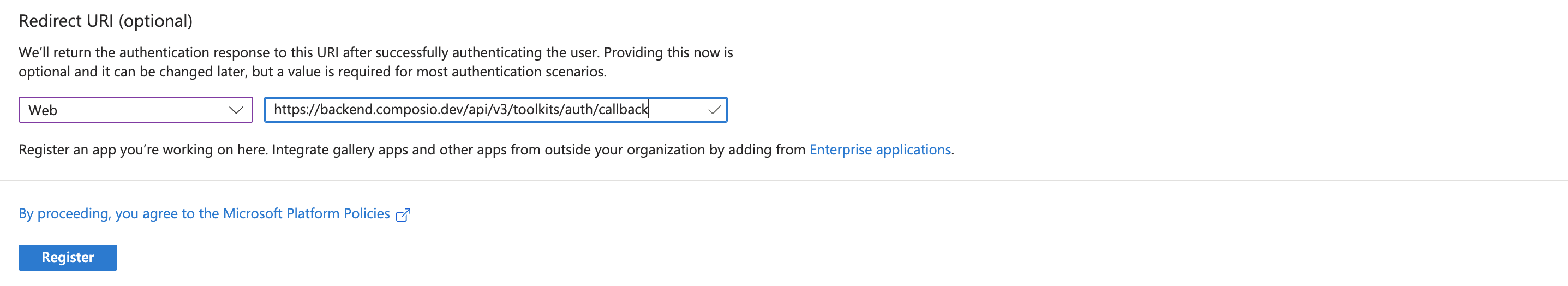
(Optional) Add call back URL. Select Web and paste your callback URL.
Then click Register.
How to Find Your Tenant ID
Go to portal.azure.com.
Search for Microsoft Entra ID.
Your Tenant ID is listed on the Overview page.
⚠️ Important: If you select "Allow all tenants" instead, any Microsoft organization will be able to authenticate with your app. Only use this if you intend for your app to be publicly accessible.
In this guide, I’ll walk through the process of setting up OAuth for Microsoft Outlook using the Azure App Registrations portal.
This lets your app connect securely to Microsoft Graph APIs (which power Outlook, OneDrive, Teams, etc.).
Note: You do not need a Microsoft 365 Developer sandbox for this. A free Microsoft personal account is enough to register an OAuth app.
Step 1: Create an Azure App Registration
Go to the Azure Portal.
In the search bar, search for App registrations and click + New registration.

Fill in your app details:

Name: Example →
Outlook IntegrationSupported account types:
Choose based on your needs:
If only your organisation would use it → Single tenant only
If multiple organisations need access → Multiple Entra ID tenants -> Allow all tenants or Allow only certain tenants (Check the Additional section for restricting access specific tenants)
If you need personal Outlook accounts too → Any Entra ID Tenant + Personal Microsoft accounts.
Redirect URI (optional): Choose Web and paste:
Click Register.
Step 2: Generate Client Credentials
Once your app is created, you’ll be redirected to its Overview page.
Copy the Application (client) ID — this is your Client ID.
From the sidebar, go to Certificates & secrets → + New client secret.
Add a description and set expiry (6 or 12 months recommended).
Copy the generated Client Secret and save it securely.

⚠️ Important: You won’t be able to see the secret again once you leave the page.
Step 3: Configure API Permissions
Now, we’ll grant the app access to Outlook data.
In the sidebar, click API Permissions → + Add a permission.
Select Microsoft Graph.
Choose Delegated permissions.
Add the required common Outlook-related scopes, such as:
Mail.Read→ Read users’ emailsMail.Send→ Send emails on behalf of the useroffline_access→ Enable refresh tokensopenid profile email→ Basic login profile
For other apps like Teams, SharePoint, Excel, etc add specific permissions
Click on Grant Admin Consent to authorise the app to call APIs.

Click Add permissions.
Step 4: Update Redirect URIs
From the sidebar, open Authentication.
Under Redirect URIs, make sure this URL is added:
Under Advanced settings, enable Allow public client flows (this makes it easier to test).
Save changes.
Step 5: Create the Auth Config in Composio
With your Client ID and Client Secret ready, head over to the Composio Dashboard.
Click Create Auth Config.

Select Microsoft Tenant (or Microsoft Teams if listed).

Choose OAuth2 as the authentication type.
Check Use your own developer authentication.
Paste in your:
Client ID → from Azure App Registration
Client Secret → from Certificates & secrets

Redirect URI →
Save the config.
Step 6: Authorize and Connect
In Composio, click Connect Account for the Outlook config.
You’ll be redirected to Microsoft’s login screen.
Approve the requested permissions (Mail.Read, Mail.Send, etc.).
Composio stores the tokens once authorization succeeds.
API Base URL
For Microsoft Graph (which powers Outlook), the base URL is:
Example endpoints:
List user emails →
/me/messagesSend email →
/me/sendMail
Once done, copy the auth config ID (which starts with ac_) and use it in your application code via a secret manager.
Scopes for Other Microsoft Apps
If you want to integrate with other Microsoft services, you can reuse the same Azure app. Just add the required scopes in both Azure and Composio:
OneDrive →
Files.ReadWrite,Files.read.allTeams →
Channel.ReadWrite.AllSharepoint →
List.ReadExcel →
Files.ReadWrite
Once scopes are added, you can configure additional auth configs in Composio for each service.
Additional: Restricting Access to Specific Tenants
If you're using your own custom OAuth app and want to limit access to only your organization's tenant or specific customer tenants, follow the steps below.
When the OAuth app is set to Multiple Entra ID tenants, it uses the /common endpoint, which means any Microsoft organisation could potentially authenticate. To restrict this, you can use the Allowed tenants setting to whitelist only specific organisations.
Step 1: Set Supported Account Type
Go to portal.azure.com and navigate to your app registration.
In the search bar, search for App registrations and click + New registration.

In the following page, you will be asked add your App name and Authentication type.

Under Authentication, click the Supported account types tab.
Select Multiple Entra ID tenants.

Step 2: Restrict to Specific Tenants
Under the Supported accounts tab, select "Allow only certain tenants (Preview)".
Click Manage allowed tenants.

Add the Tenant ID of each organisation you want to allow.

Click Apply.
(Optional) Add call back URL. Select Web and paste your callback URL.
Then click Register.

How to Find Your Tenant ID
Go to portal.azure.com.
Search for Microsoft Entra ID.
Your Tenant ID is listed on the Overview page.
⚠️ Important: If you select "Allow all tenants" instead, any Microsoft organization will be able to authenticate with your app. Only use this if you intend for your app to be publicly accessible.

